This article gives some insights on how to set up a network traffic analysis and alerting system based on NetFlow....
SD-WAN and NetFlow
Software-Defined Networking (SDN) in a Wide Area Network (WAN) - SD-WAN is a technology that simplifies management of...
Identifying, monitoring and securing BYOD traffic with NetFlow
Bring Your Own Device (BYOD) is a practice that allows users to bring their personal devices such as tablets or...
Finding MAC addresses using Flexible NetFlow
So far, we have discussed NetFlow configuration for network devices from various vendors such as Cisco, Juniper,...
Web Applications compromise detection using Flow Data
Our previous article discusses flow-based SSH compromise detection. A force attack against SSH hosts consists of scan,...
SSH Compromise Detection Using Flow Data
Secure Shell (SSH) provides a secure channel over an unsecured network in a client-server model. SSH is typically used...
DNS Amplification Attacks Detection with NetFlow or sFlow
The Internet we know nowadays cannot properly operate without using the Domain Name System (DNS). DNS syncs up domain...
The Difference between SNMP and NetFlow. Why should I use both?
Simple Network Management Protocol (SNMP) is a well-known standardized application layer protocol, originally...
Automatic versus Manual NetFlow Deduplication
Duplication of NetFlow occurs when the NetFlow records about the same flow are exported multiple times to a NetFlow...
Exporting Flow to multiple servers (Flow Samplicators)
In our previous article we have discussed the alternative way to get flow statistics using a NetFlow generator. One of...
NetFlow Generators explained
What is a NetFlow Generator? A NetFlow generator is a dedicated network appliance or software running on a PC and...
Configuring NetFlow on VyOS and Huawei Network Devices
This is the second part of the post dedicated to NetFlow configuration. In the first part, we’ve discussed the...
Configuring Cisco Flexible NetFlow and Juniper j-Flow v8
One of our recent blog posts dedicated to NetFlow technology provides the necessary knowledge needed to understand...
The accuracy and overhead of flow sampling. To use or not to use flow sampling?
Flow-based (NetFlow, IPFIX, NetStream) and packet-based (sFlow) network monitoring technologies enable network...
NetFlow vs. sFlow vs. IPFIX vs. NetStream. Network Traffic Analysis and Network Traffic Monitoring.
Network monitoring is a systematic effort to monitor parameters of a computer network in order to detect issues that...
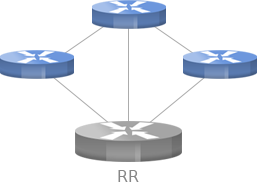
Route Reflectors – an alternative to full-mesh iBGP configuration
The typical fully-meshed iBGP configuration of routers can become very difficult to manage in large networks. Because...