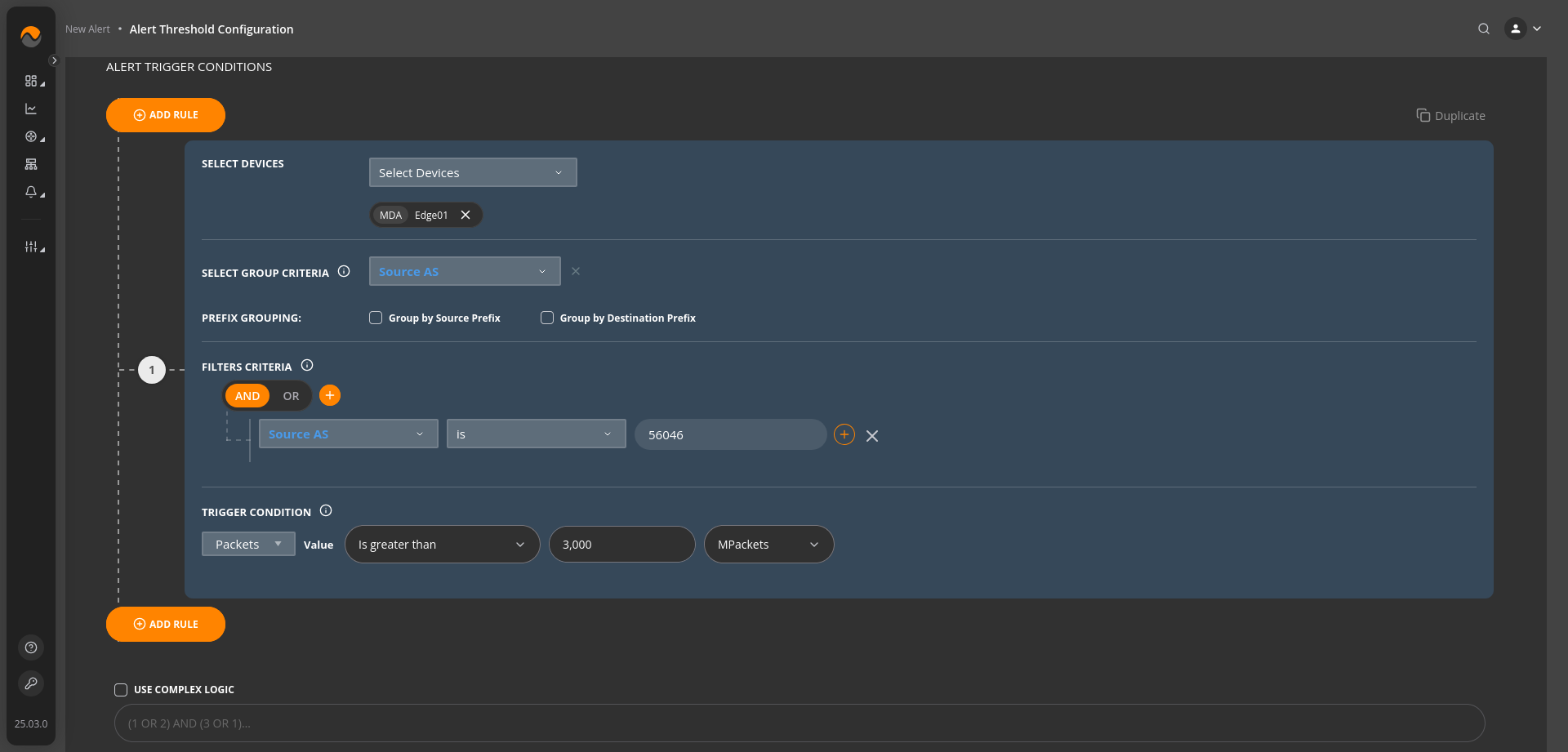
Alert Name: High Packet Volume from Source AS 56046 #
Description: This alert triggers when the number of packets sent from Source AS (Autonomous System) 56046 exceeds 3000 Mega packets (Mpackets). This condition indicates a significant volume of traffic directed towards AS 56046, which may warrant further investigation to ensure network stability and security.
Alert Priority: Critical Priority.
Filters Criteria: Source AS is 56046.
Trigger Condition: Packets Value Is greater than 3000 MPackets.
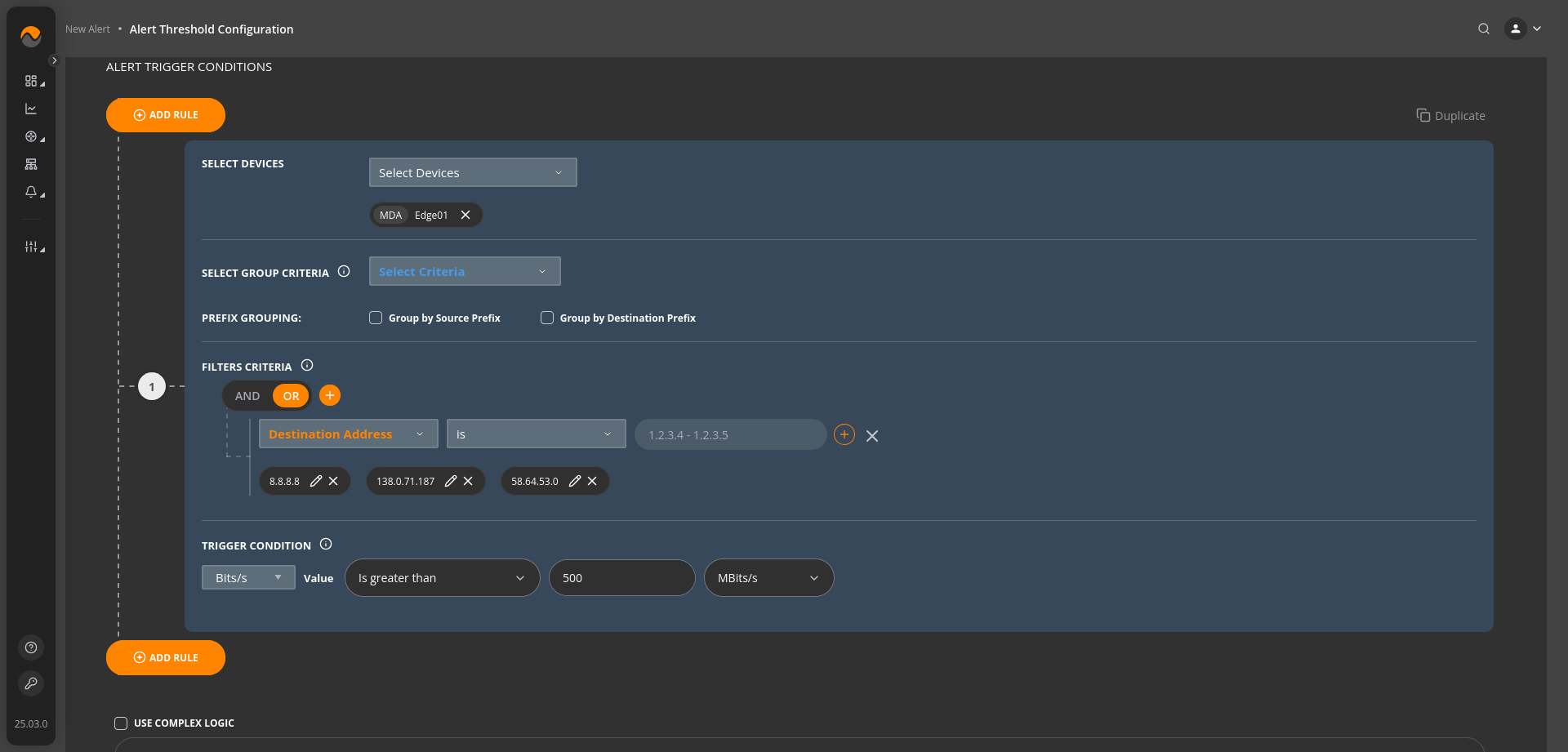
Alert Name: High Traffic Volume to Specific IP Addresses #
Description: This alert triggers when the traffic to any of the specified destination IP addresses (8.8.8.8, 138.0.71.187, or 58.64.53.0) exceeds 500 Megabits per second (MBits/s). This condition indicates a high volume of traffic directed towards these IP addresses, which may indicate unusual activity or potential issues that require attention.
Alert Priority: Critical Priority.
Filters Criteria: Destination Address is 8.8.8.8 OR 138.0.71.187 OR 58.64.53.0
Trigger Condition: Bits/s Is greater than 500 MBits/s.
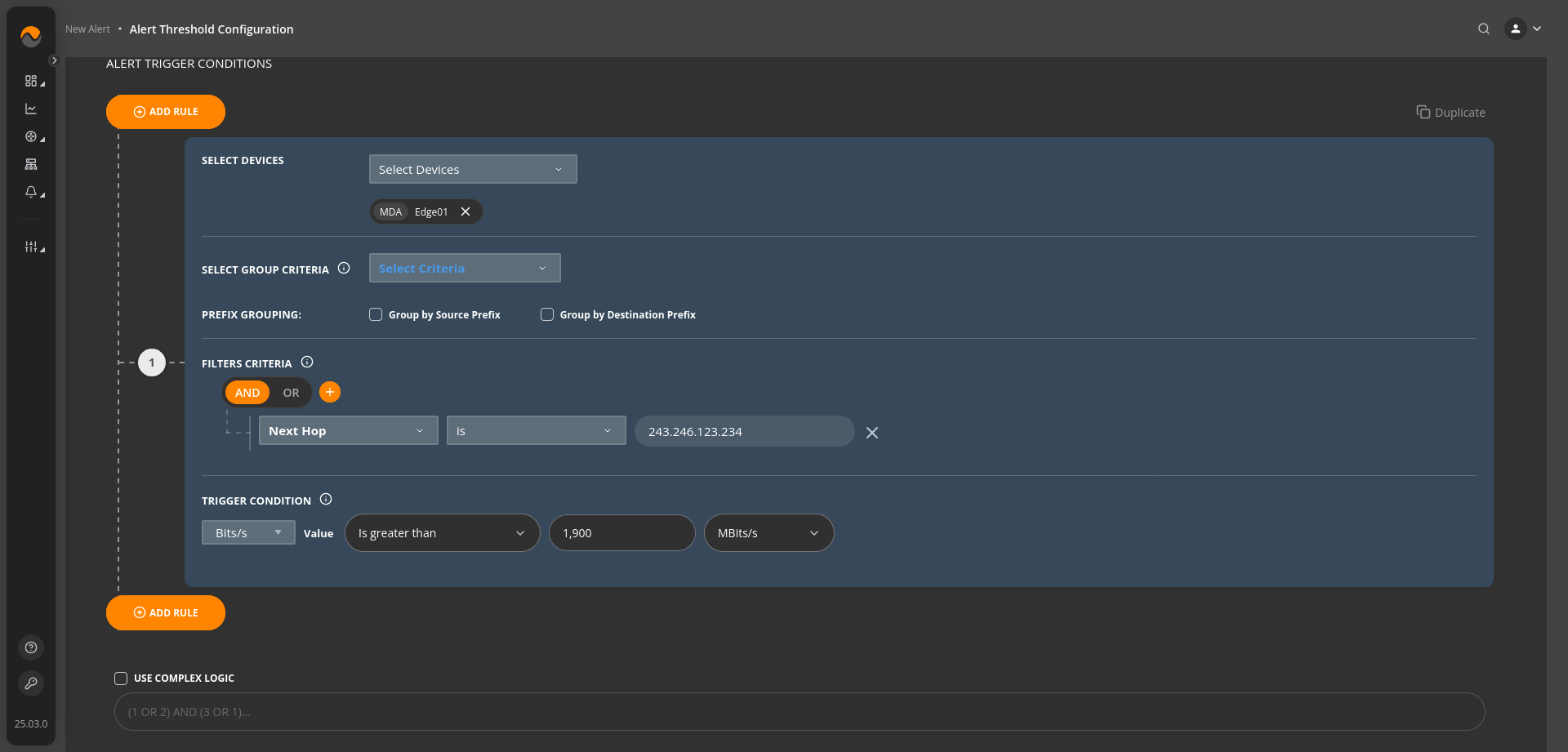
Alert Name: Circuit getting overutilized/Circuit close to being overutilized #
Description: Alert will trigger if the traffic with next_hop 243.246.123.234 exceeds 1900 Mbps.
Alert Priority: Critical Priority.
Filters Criteria: Next Hop is 243.246.123.234.
Trigger Condition: Bits/s value Is greater than 1900 MBits/s.
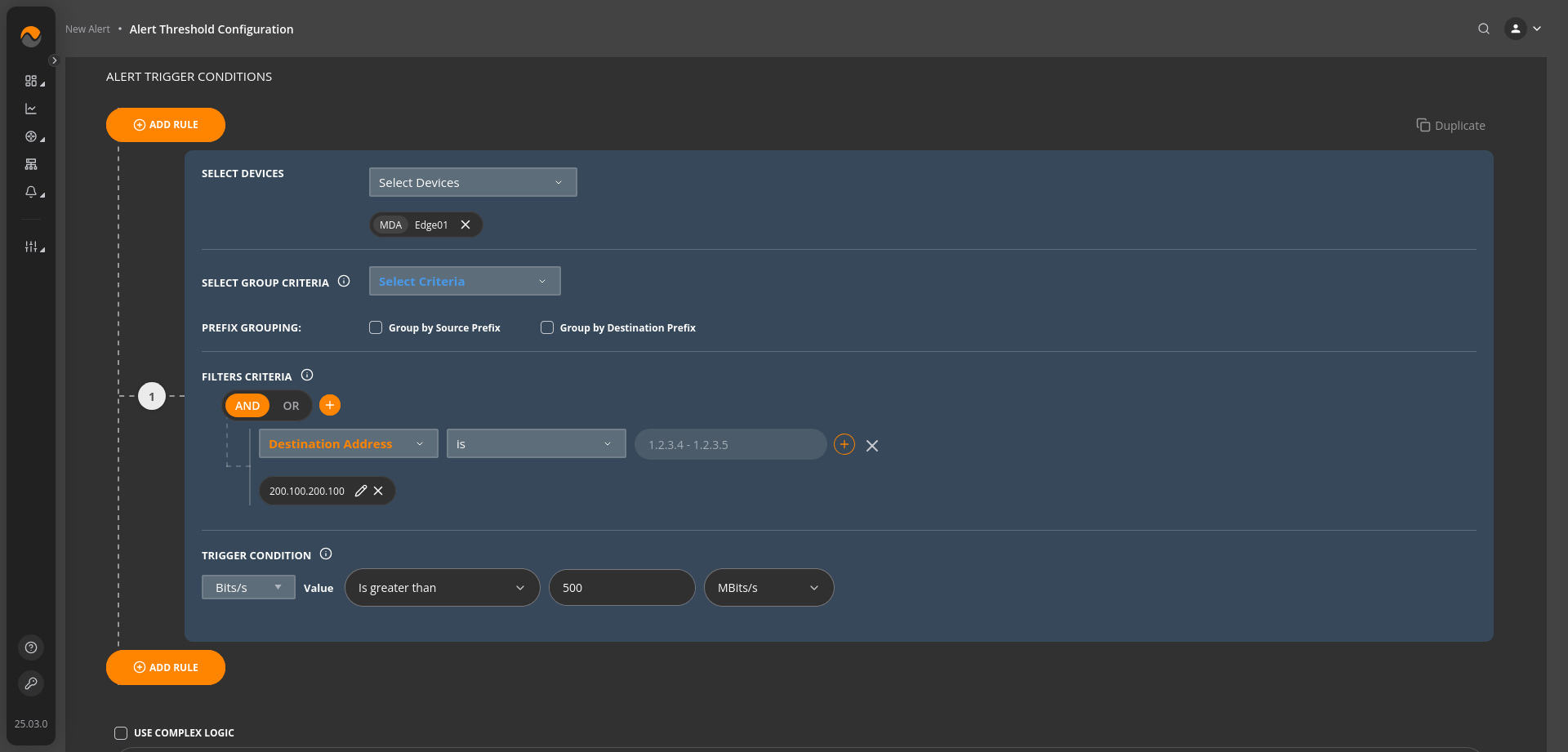
Alert Name: Possible Threshold based DDoS attack on server/network equipment.
#
Description: Alert will trigger if the traffic with destination address is a Server or a Network equipment that is offering services ( we’ll use 200.100.200.100 as example for a web server ) exceeds 500 Mbps.
Alert Priority: Critical Priority.
Filters Criteria: Destination Address is 200.100.200.100.
Trigger Condition: Bits/s value Is greater than 500 MBits/s.
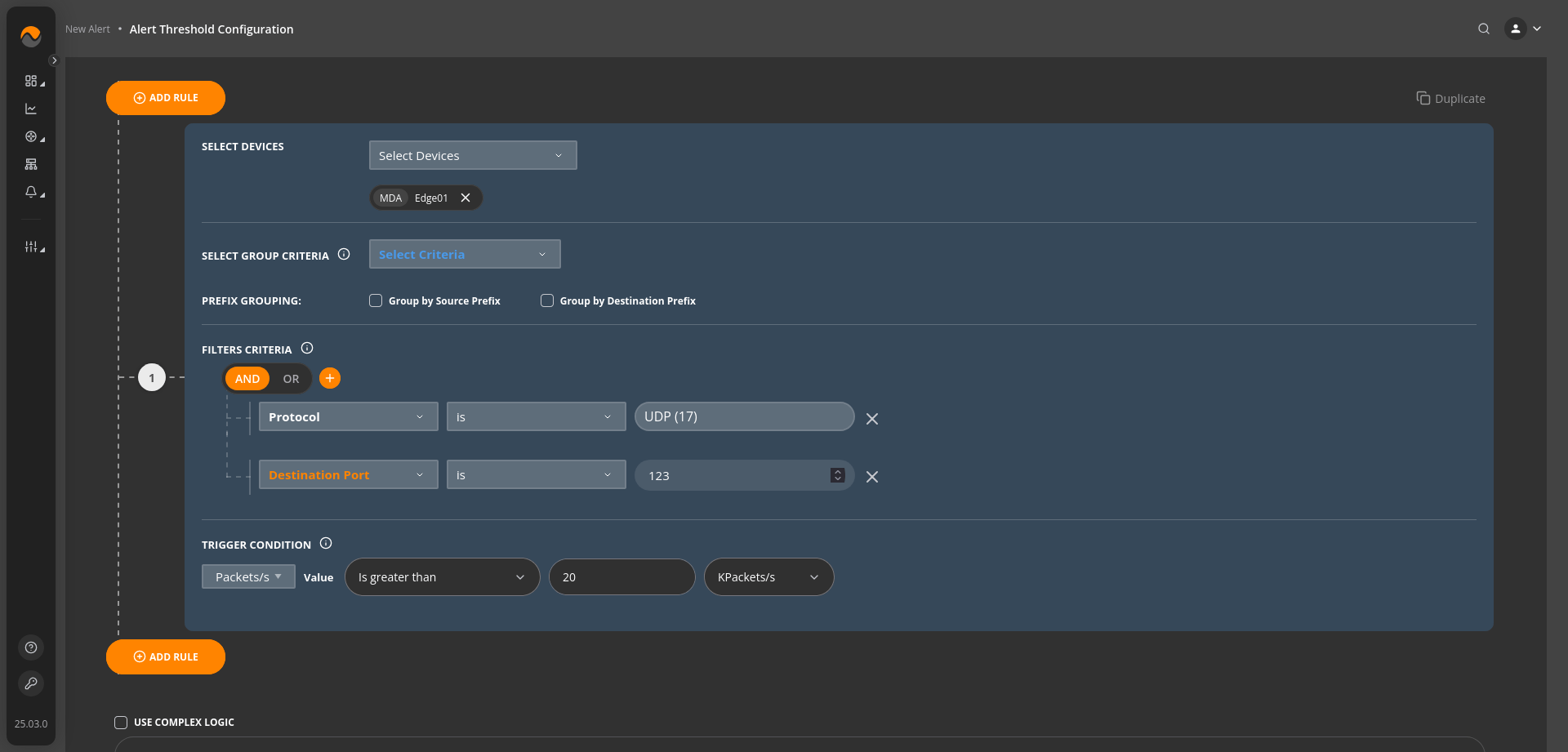
Alert Name: NTP Amplification Attacks #
Description: This alert triggers when the rate of UDP packets per second directed to destination ports 123 (NTP or other custom NTP port that you’re using) exceeds 20,000 packets per second (KPackets/s). This condition indicates a significant volume of UDP traffic targeting these ports, which may suggest unusual network activity or a potential NTP-based amplification attack. Immediate investigation is necessary to ensure the security and stability of the network.
Alert Priority: Critical Priority.
Filters Criteria: Protocol is UDP AND Destinaion Port is 123.
Trigger Condition: Packets/s value Is greater than 20 KPackets/s.
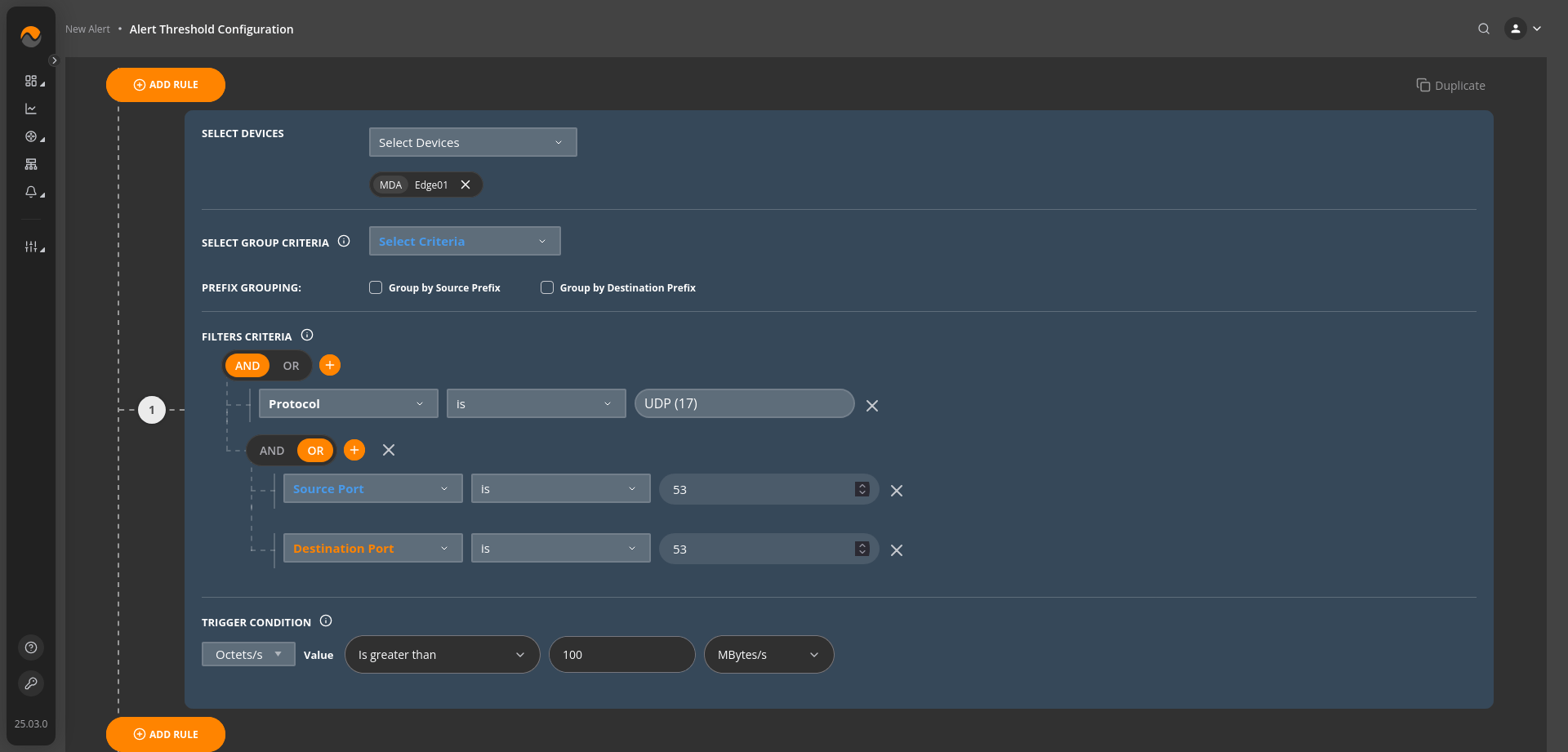
Alert Name: High UDP Traffic on DNS Port #
Description: This alert triggers when the data transfer rate of UDP traffic directed to destination port 53 or originating from source port 53 exceeds 100 Megabytes per second (Mbytes/s). Port 53 is commonly used for DNS (Domain Name System) queries, and a high data rate may indicate unusual DNS traffic patterns or a potential DNS amplification attack. Immediate investigation is required to ensure network security and proper functioning of DNS services.
Alert Priority: Critical Priority.
Filters Criteria: Protocol is UDP AND (Destination Port is 53 OR Source Port is 53).
Trigger Condition: Bytes/s value Is greater than 100 Mbytes/s.
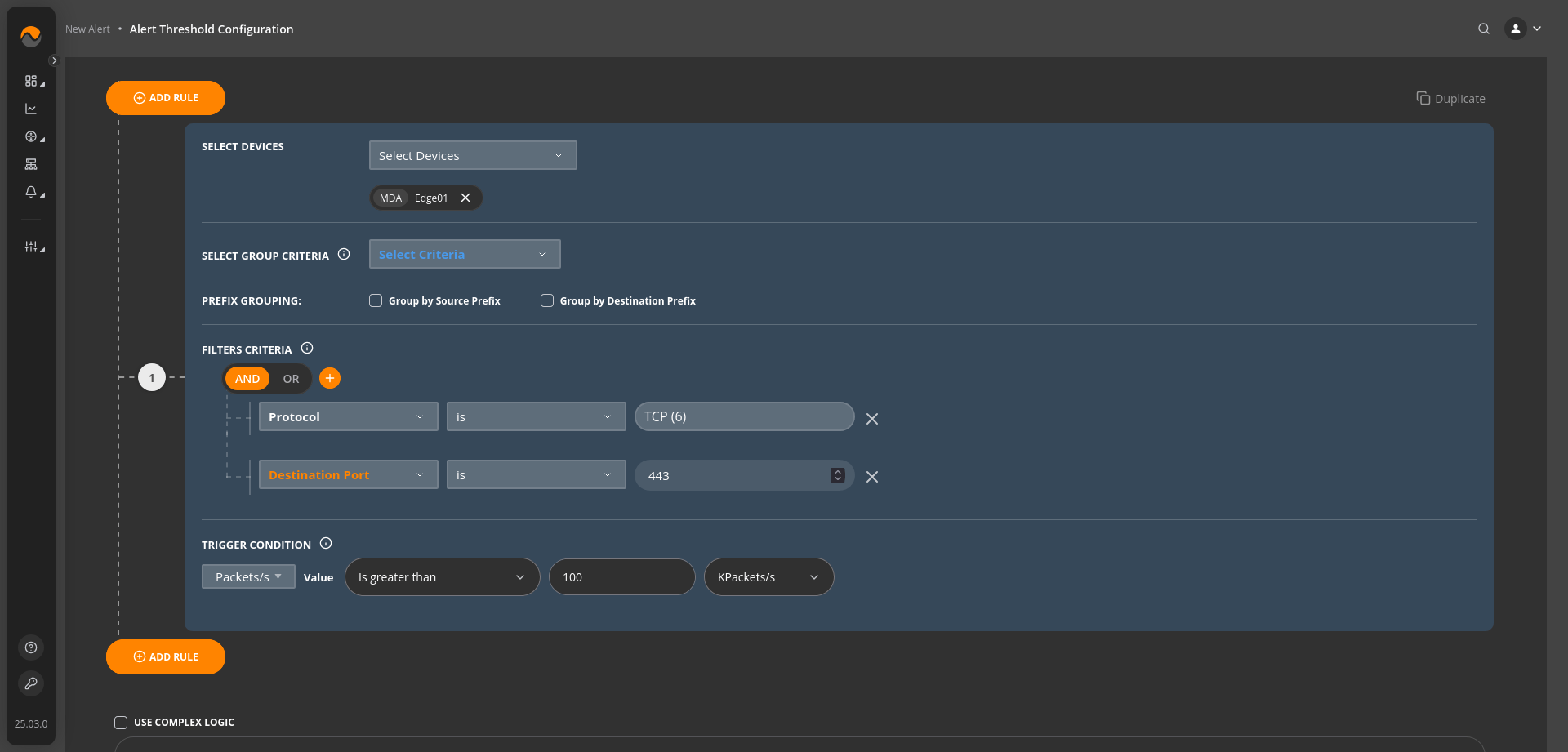
Alert Name: Browser-Based Bot Attack Detection (DDoS) #
Description: This alert triggers when the rate of TCP packets directed to destination port 443 exceeds 100,000 packets per second (KPackets/s). Port 443 is commonly used for HTTPS (secure web traffic), and such a high packet rate may indicate a potential browser-based bot attack (DDoS), where automated scripts or bots generate excessive traffic to disrupt secure web services. Immediate investigation is required to mitigate the impact and ensure the security and availability of web resources.
Alert Priority: Critical Priority.
Filters Criteria: Protocol is TCP AND Destinaion Port is 443.
Trigger Condition: Packets/s value is greater than 100 KPackets/s.
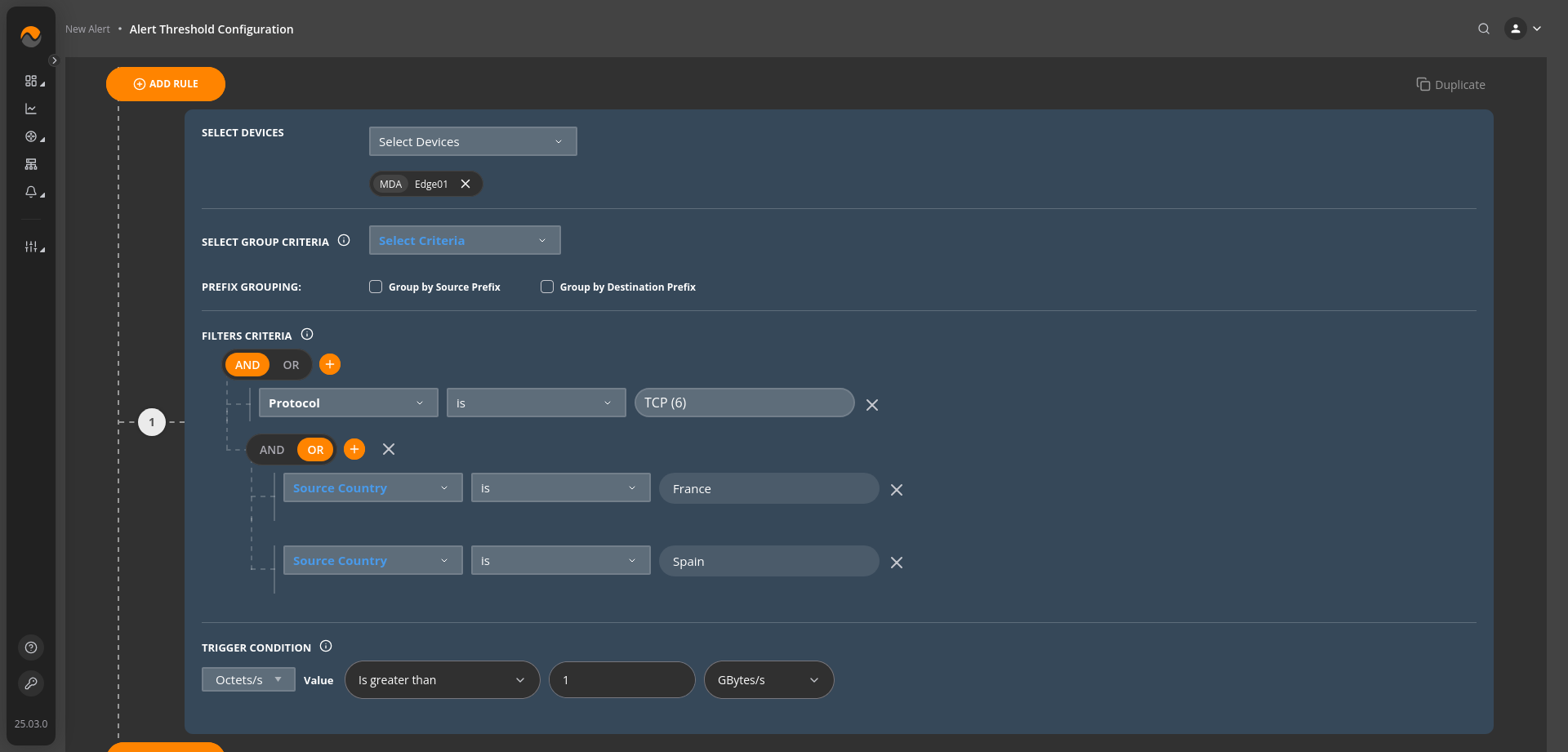
Alert Name: Country Based Attacks #
Description: This alert triggers when the data transfer rate of TCP traffic originating from France or Spain exceeds 1 Gigabyte per second (GBytes/s). This condition indicates a significant volume of TCP traffic from these countries, which may require attention to ensure network performance and security. Immediate investigation is recommended to understand the nature and purpose of this high traffic and take appropriate actions if necessary.
Alert Priority: Critical Priority.
Filters Criteria: Protocol is TCP AND (Source Country is France OR Source Country is Spain).
Trigger Condition: Octets/s Is greater than 1 GBytes/s.
* The amount of Packets/s, Bits/s, Bytes/s varies from network to network, this value has to be monitored during normal business hours where traffic is at its peak. Once the maximum normal amount of traffic is identified, the threshold can be properly set up.