flow record NETFLOW-RECORD match ipv4 source address match ipv4 destination address match ipv4 protocol match transport source-port match transport destination-port match ipv4 tos match interface input collect counter bytes collect counter packets collect interface output flow exporter NETFLOW-EXPORTER1 destination 192.168.3.1 source GigabitEthernet0/0 transport udp 2055 template data timeout 60 flow exporter NETFLOW-EXPORTER2 destination 192.168.4.1 source GigabitEthernet0/0 transport udp 2055 template data timeout 60 flow monitor NETFLOW-MONITOR record NETFLOW-RECORD exporter NETFLOW-EXPORTER1 exporter NETFLOW-EXPORTER2 cache timeout active 30 cache timeout inactive 15 interface GigabitEthernet0/1 ip flow monitor NETFLOW-MONITOR input
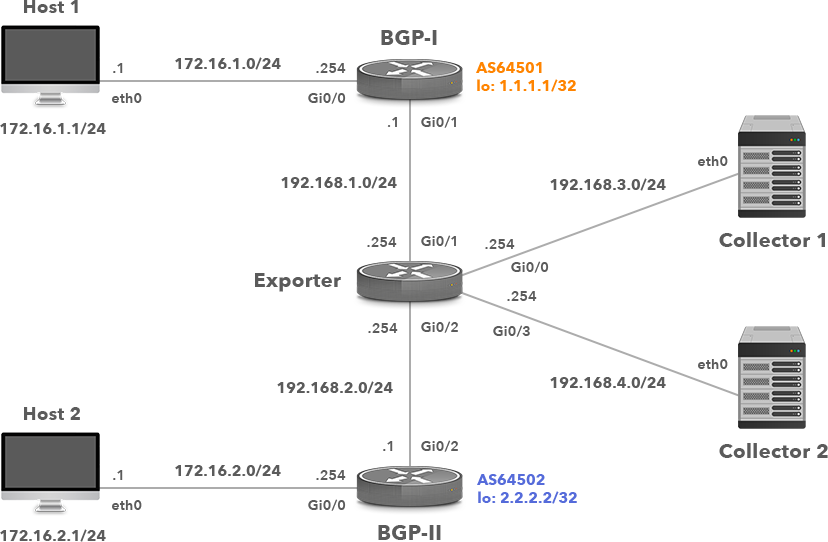
Picture 1: Network Topology with NetFlow Exporter and Two Collectors
However, some network devices do not support the exporting of flow records to multiple locations. In this case, we can use a workaround in the form of a flow samplicator inserted between a NetFlow exporter and collectors. A NetFlow samplicator is a program that receives UDP datagrams on a given port from a single or multiple senders (NetFlow exporters) and resends those datagrams to a specified set of receivers (NetFlow collectors).
To demonstrate the function of a NetFlow samplicator, we will replace a flow exporter running Cisco IOS with a VyOS appliance (Picture 2). The appliance with the IP address 192.168.3.254/24 is located in the middle of a network topology and is configured to operate as a NetFlow exporter. It does not support flow exporting to multiple locations. Therefore, the VyOS appliance exports flow records version 9 to the NetFlow samplicator that is listening on the IP address 192.168.3.2 and the UDP port 2055. It is a job of the samplicator to redistribute NetFlow traffic (UDP datagrams) to the configured receivers.
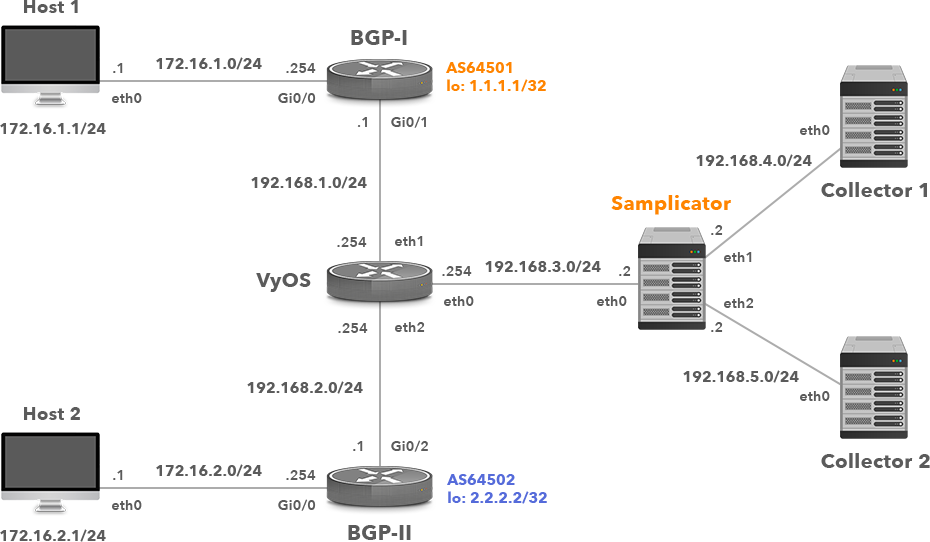
Picture 2: Network Topology with a NetFlow Exporter, Samplicator and Two Collectors
Below is the configuration related to NetFlow v9 on VyOS.
system {
config-management {
commit-revisions 100
}
console {
device ttyS0 {
speed 9600
}
}
flow-accounting {
interface eth1
netflow {
sampling-rate 100
server 192.168.3.2 {
port 2055
}
timeout {
expiry-interval 60
flow-generic 3600
icmp 300
max-active-life 604800
tcp-fin 300
tcp-generic 3600
tcp-rst 120
udp 300
}
version 9
}
syslog-facility daemon
}
}
Let’s start NetFlow samplicator and check if it is listening on the socket 192.168.3.2/2055 (Picture 3).
$ sudo samplicate -s 192.168.3.2 -S -p 2055 -d 192.168.4.1/2055 192.168.5.1/2055
-b Set socket buffer size ( default 65536) -c Specify a config file to read. -d Debug level -f Fork. This option sets samplicate to work as background process. -n Do not compute UDP checksum (leave at 0) -p <port> UDP port to accept flows on (default 2000) -S Maintain (spoof) source address. -s <address> Interface address to accept flows on (default any) -x <delay> Transmission delay in microseconds.
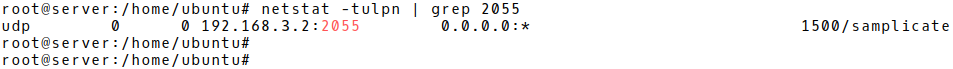
Picture 3: Checking Whether Samplicator is Listening on IP address 192.168.3.2 UDP 2055
Soon after the NetFlow samplicator is started, we should see the debugging messages (Picture 4) in the console. The samplicator resends NetFlow records received from the NetFlow exporter with the IP address 192.168.3.1, the source port 39268 as UDP datagrams to NetFlow collectors 192.168.4.1 and 192.168.5.1, the destination UDP port 2055.
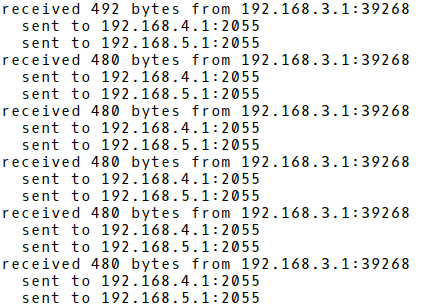
Picture 4: Captured Debugging Output from Samplicator CLI
Use Wireshark or tcpdump to open the pcap files captured on both collectors and explore. When we reviewed both captures properly, we could see that flow records contained many flows, counting a single IP packet that has been sent from different source IP addresses to the destination IP address 172.16.2.1 (Picture 5). Those are TCP segments with SYN flag set, sent from the spoofed IP address 172.16.1.1/24 in order to prevent legitimate users to access SSH service (TCP port 22), running on the host 172.16.2.1. Notice, the source IP address of NetFlow exporter 192.168.3.1. This is the IP address of the VyOS router. As the samplicator is configured with the option -S (spoof source address), it preserves the IP address of the original Netlow exporter (VyOS). Therefore, the IP address configured on the network interface of a UDP samplicator – 192.168.4.2 is not used.
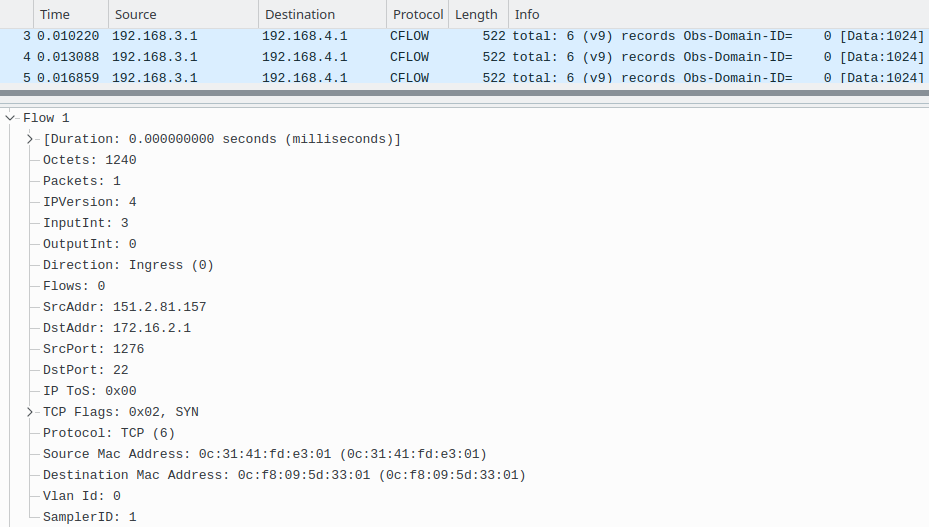
Picture 5: Wireshark Capture Screen on NetFlow Collector1
Conclusion:
Ideally, flow exporters should be able to export flow records to multiple destinations. In reality, many network devices with a built-in NetFlow feature can export them only to a single or at most two flow collectors. Luckily, a hack in the form of a UDP samplicator can be used as a great workaround. Running as a virtual appliance or on physical hardware, samplicators resend UDP streams to multiple receivers. The number of receivers is only limited by hardware resources of the samplicator appliance, such as CPU and RAM. The resources of the built-in NetFlow exporters are also saved and performance kept as they do not need to export to multiple locations. Instead, flow export is off loaded to a dedicated appliance.