Flexible NetFlow allows users to configure and customize the information that is exported. It also enables the export of Layer2 fields such as MAC addresses and VLAN IDs from traffic. Let’s have a simple network topology consisting of Cisco multilayer switch that is configured as a Flexible NetFlow exporter (Picture 1). The switch collects information about inter-VLAN traffic between VLAN 10 and 20 (PC1, PC2, and PC3) and traffic sent from the VLAN subnets to the Internet. NetFlow records are exported to the collector 192.168.30.10/24, UDP port 2055. The ports Gi0/0 and Gi0/1 are configured as routed ports; all other interfaces are switch ports configured with access to either VLAN 10 or 20.

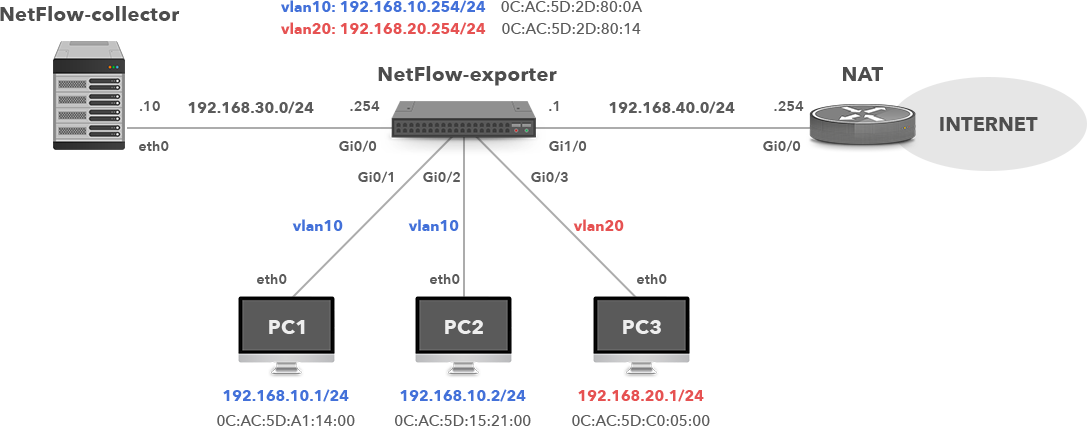
Picture 1: Network Topology
| Note: Before you start with the Flexible NetFlow configuration, you need to be sure that a NetFlow collector accepts layer 2 information and it can display it. |
In general, Flexible NetFlow consists of 3 components:
1) Flow Record
2) Flow Exporter
3) Flow Monitor
The following is a set of commands for a Cisco multilayer switch in order to enable Flexible NetFlow on the interfaces VLAN 10 and VLAN 20, with the flows exported to the collector 192.168.30.10.
Create a new customized flow record MAC_RECORD. A customized flow record must have at least one match criterion for use as the key field and typically has at least one collect criterion for use as a nonkey field.
flow record MAC_RECORD match datalink mac source address input match datalink mac destination address input match ipv4 protocol match ipv4 source address match ipv4 source mask match ipv4 destination address match ipv4 destination mask match transport source-port match transport destination-port match interface input match interface output collect counter bytes collect counter packets collect timestamp sys-uptime first collect timestamp sys-uptime last
Create a new flow exporter MAC_EXPORT. Define IP address and the UDP port of the NetFlow collector, the interface used for the flow export and the timeout for template export in seconds.
flow exporter MAC_EXPORT description flexible NetFlow version 9 destination 195.165.30.10 source GigabitEthernet0/0 transport udp 2055 template data timeout 60
Create a new flow monitor MAC_MONITOR. Assign the flow record MAC_RECORD and the flow exporter MAC_EXPORT to the flow monitor.
flow monitor MAC_MONITOR description MAC Addresses Monitor exporter MAC_EXPORT cache timeout active 30 record MAC_RECORD
Apply flow monitor MAC_MONITOR to input traffic for VLAN10 and 20 interfaces. In case you want NetFlow to cover unicast intra-VLAN traffic, you have to apply a flow monitor to physical switchports, e.g GigabitEthernet0/1.
interface Vlan10 ip flow monitor MAC_MONITOR input ip address 192.168.10.254 255.255.255.0 interface Vlan20 ip flow monitor MAC_MONITOR input ip address 192.168.20.254 255.255.255.0
The first flow record in the NetFlow cache of the switch is depicted in Picture 2. It includes traffic statistics about ICMP packets sent from PC3 – 192.168.20.1 in VLAN20 (MAC address 0CAC.5DC0.0500) to PC1 – 192.168.10.1 in VLAN10. The MAC address 0CAC.5D2D.8014 is the MAC address of the VLAN20 interface. This is correct as Layer2 headers are always changed by a Level3 network device (router or a multilayer switch) when packets are forwarded between different Layer3 broadcast domains. The flow contains 29 ICMP packets (IP protocol 1) with 2436 bytes along with additional information such as timestamps and source/destination prefixes /24.
Picture 2: Flow Record in Exporter’s Cache with ICMP Traffic
TCP traffic (IP protocol 6) sent from the host PC3 (192.168.20.1/24), VLAN20 to the Internet (2.21.77.152) is depicted on Picture 3. More particularly, it is HTTPS traffic (destination TCP port 443) sent from PC3 via the interface GigabitEthernet1/0 to the network assigned to Akamai International B.V., BGP AS number 20940.
Since broadcast traffic from hosts in a particular VLAN hits a VLAN interface of the switch, we can obtain information about broadcast traffic, as well. The flow record shown in Picture 4 depicts DHCP DISCOVER message sent from the host PC1 (0CAC.5DA1.1400), source UDP port 68, to all hosts in VLAN10, (MAC address FFFF.FFFF.FFFF), destination UDP port 67. This is the first message in a series of DORA (Discover, Offer, Request, Assign) messages that PC1 is using to obtain an IP address from DHCP server in VLAN10 subnet.
Picture 3: Flow Record with HTTPS Traffic
Picture 4: Flow Record with DHCP Request Message
If we need to show the volume of traffic leaving VLAN networks per host along with broadcast traffic, we can aggregate flow records based on the source MAC and IP address fields (Picture 5). The host 192.168.20.1 (PC3) is a top talker with the most packet and byte counts but with the lowest number of flows equal 2. The higher number of flows with a small number of bytes and packets for hosts in VLAN 10 (192.168.10.0/24) indicates that the hosts perform a certain scan type (ICMP or TCP).
Netflow-exporter# show flow monitor MAC_MONITOR cache aggregate datalink mac source address input ipv4 source address
Picture 5: Aggregated Flow Records based on Source MAC and IP Addresses
Notice the higher number of consecutive 1-packet flows with source IP address 192.168.10.2 (MAC 0CAC.5D15.2100) and destination IP address from the subnet 200.11.1.0/24, destination TCP ports 80, 443 in the report Nmap_Scan_Internet.pdf. It confirms that PC2 is conducting a TCP scan in order to detect web servers in the IP address space assigned to Universidade Federal Rural do Rio de Janeiro. The number of bytes per flow is flat – always counting 60 Bytes.
The second report MAC_flooding_attack.pdf shows a huge number of flows that count one packet with a constant number of 20 bytes. The source MAC address and source/destination IP addresses differ for each flow. Furthermore, flows are generated by a host in the VLAN 20. In fact, the report contains flow records collected during a MAC address flooding attack. The attack is conducted against the switch with the aim to consume a limited switch memory where learned MAC addresses are temporally stored. Once the CAM memory is full, the switch acts as a primitive hub, sending frames out of each port. As a result, an attacker can be successful in eavesdropping conversations or crashing the switch.
Unlike IP addresses, that are very often dynamically allocated, MAC addresses are unique identifiers that can be used to reliably identify hosts in your network. Flexible NetFlow allows users to collect VLAN IDs or MAC addresses. Therefore, if your current NetFlow collector supports this feature, configure Flexible NetFlow to collect Layer 2 information. It gives you an ability to correlate IP and MAC addresses in the process of hosts identification.