Border Gateway Protocol (BGP) is not merely a protocol—it’s the backbone of the...


Cryptocurrency is a digital asset that works as a medium of exchange. It uses cryptography to secure transactions and to control the creation of additional units of the currency. Bitcoin is the oldest and the most known cryptocurrency, launched in 2009. For this reason, the article aims at explaining it principles and network attacks against the Bitcoin network. Bitcoin is often called digital gold because its amount is limited. The number of Bitcoins (BTC) does not exceed 21 million (20 999 999,9769). It is the first decentralized digital currency. It means that no central authority such as government or a bank controls Bitcoin.
Bitcoin can be sent from one Bitcoin wallet to another one using Bitcoin addresses, just like emails are sent. This process is called a transaction. Senders broadcast transactions to the Bitcoin network. Miners collect transaction records, verify the transaction putting it into a transaction block and try to solve the block they are working on. Once a block is solved, it is sent to other Bitcoin nodes where it is recorded to the blockchain. The blockchain is a chain of all blocks and each block contains a reference to a previous one. Thanks to blockchain, Bitcoin nodes have information about all historic Bitcoin transactions.
Miners are motivated to solve a block by a combination of transaction fees (paid by the sender) and a block reward. If a block contains only a single transaction, there are no transactions to be mined. In this case only the mining reward goes to the miner. Solving a block involves computing a hash (double-SHA-256) of the block header that miners are working on. The block header contains the reference to a previous block (a hash of the previous block in the blockchain), a merkle root (the hash of the hashes of all transaction inside transaction block), version, timestamp, bits and a random integer number called a nonce. The block number 42000 is shown in picture 1. It contains only a single transaction.
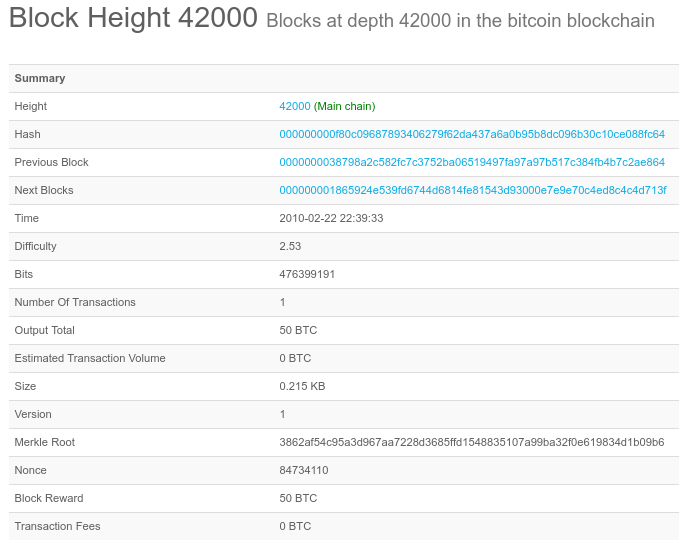
Picture 1: Bitcoin Block Number 42000
The goal is to compute a hash that has a certain number of zeros. More leading zeros means fewer possible solutions, which increases the required time to find a required hash. For instance, a block number 488582 contains 18 leading zeros in the computed hash, the nounce is 1744886609 and the block contains 567 transactions. The reward for solving the block is 12.5BTC. If a computed hash does not contain the right number of leading zeros, the nonce is changed and the hash is computed again.
It is now extremely hard to solve a block by a single miner. Computation of massive number of hashes consumes a lot of mining power due to high block difficulty. Difficulty is a measure of how difficult it is to find a new block. For this reason, miners cooperate and they group into mining pools. Block reward is then shared between miners in proportion to their contributed mining hash power. Bitcoin block reward was originally 50 BTC and it is currently 12.5 BTC. It halves every 210,000 blocks so it will decrease to 6.25 BTC with the block 630,000. The first block in the blockchain has 8 leading zeros with the difficulty 1. Difficulty changes every 2016 blocks (approximately every 14 days). Summary statistics can be found here.
Let’s have a look at the location of Bitcoin nodes and top mining pools in the Internet. Bitcoin nodes are computers that are connected to the Bitcoin peer-to-peer network. Computers running the Bitcoin Core client with the complete blockchain are called full nodes. Bitcoin full nodes validate and relay transactions, broadcasting messages across a network, establishing random peer-to-peer connection in the Bitcoin network. The Bitcoin reachable nodes have opened port 8333. According to the snapshot of the reachable Bitcoin nodes made on Thursday Oct 05 2017, there were 9609 Bitcoin nodes around the globe. Precisely 66,47% of all Bitcoin nodes were concentrated in six countries, with the United States at the top of the ladder with 28,08%.
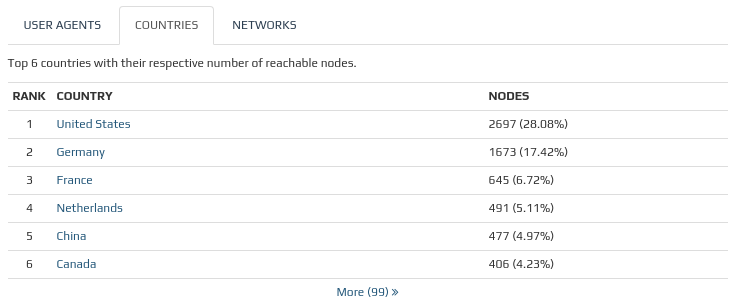
Picture 2: Top Six Countries With Their Respective Number of Reachable Nodes
https://bitnodes.21.co/nodes/
It is worth to mention the location of mining power around the globe. Not surprisingly, the largest six mining pools are located in China – AtnPool: 21,7%, F2Pool: 11,1%, BTC.com: 10,6%, BTC.TOP: 9,3%, viaBTC: 8,9% and BTCC Pool: 8,4%. These mining pools have massive computing power and they mine approximately 70% of all new bitcoins.
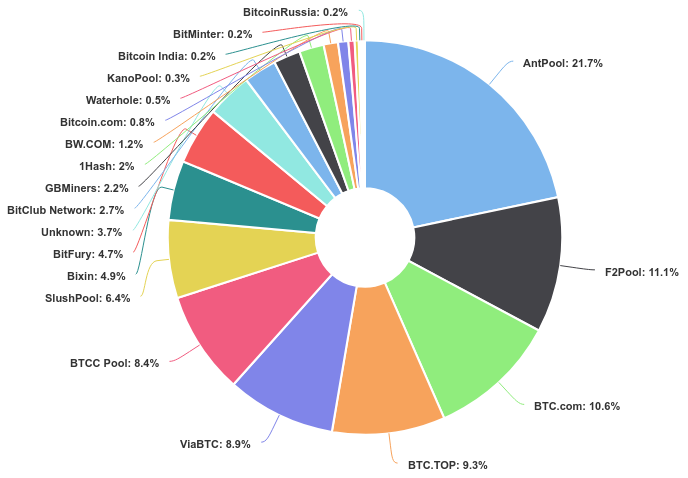
Picture 3: Top Mining Pools
https://blockchain.info/pools
Obviously, the mining power is centralized to certain mining pools and the majority of Bitcoin nodes are located in a few countries. Based on collecting BGP data from October 2015 to March 2016, PhD student Maria Apostolaki (ETH Zürich university) in her research paper states, that only 13 Autonomous Systems (ASes) host 30% of the entire Bitcoin network, while 50 ASes host 50% of the Bitcoin network. She also reveals that three Tier-1 providers (Hurricane Electric, Level3, and Telianet), can together intercept more than 60% of all possible Bitcoin connections. It is another excellent proof that the Bitcoin network is highly centralized from a routing point of view.
This centralization brings undesired consequences in the form of susceptibility of the Bitcoin network to certain types of network-based attacks, as it is easier to conduct a network attack against a centralized network than a peer-to-peer network. In the next parts, we will discuss the partition and delay attacks using BGP. These attacks are very well documented in Apostalaki’s research paper including detailed statistics.
The partition attack includes isolation of a victim Bitcoin node from the Bitcoin network. Traffic from/to the attacked Bitcoin nodes is deliberately blackholed by an attacker in a certain point of the Internet. The attacker effectively splits the Bitcoin network into two isolated components that have no connectivity between each other. As a result, the block is solved in both components (the new block is solved approximately every 10 minutes) and it is broadcasted toward other Bitcoin nodes within components. Afterwards, the attacker stops the attack and connectivity between components is regained. However all blocks mined within the smaller component (with less mining power) will be discarded, along with all transactions and the miners revenue. Therefore, the consequences of partition attacks are Denial of Service (DoS) for the Bitcoin clients in a smaller component and the loss of revenue. Moreover, transactions in a smaller component can be reverted (double spending).
In order to blackhole traffic of the targeted Bitcoin nodes, the attacker exploits the weakness of the BGP protocol. As a result, the attacker effectively hijacks IP prefixes where Bitcoin nodes are located. As we know, BGP does not validate whether an origin AS is eligible to announce a prefix. Therefore, an attacker who gains access to an ISP router can announce any prefix via BGP. Let’s say that the attacker announces a prefix with the same length (partial BGP hijacking) as the owner of the prefix but AS_PATH attribute is shorter (fewer AS hops) than the AS_PATH in the original BGP announcement. As a result, the newer prefix, announced by the attacker AS, is installed into routing tables.
However, it is more effective for the attacker to announce a more specific prefix. In that case a complete BGP hijacking situation occurs, as BGP routers install more specific routes into their routing tables. As Maria Apostolaki in her paper claims, the vast majority of Bitcoin nodes are hosted in prefixes less than /24. Therefore, an attacker is announcing prefixes with length /24. Prefixes longer than /24 would be very likely filtered by upstream providers.
Note: We dedicated an entire article to BGP hijacking and countermeasures. However, the Bitcoin network could become significantly less prone to this type of hijack by better decisions being taken to initial announcements.
The delay attack is another type of network attack against the Bitcoin network using BGP hijacking. The attack effectively slows down propagation of blocks towards a victim. The goal is to delay a delivery of a new block to a victim, keeping the victim uninformed for almost 20 minutes about a new block. Contrary to the partition attack, the attacker does not blackhole a victim’s connection. Instead, BGP hijacking is used to conduct a Man-in-the-Middle attack (MITM) between a victim and its peer. The attacker also needs to modify Bitcoin messages sent from the victim to the peer in order to perform a successful delay attack.
When a new block is mined, a Bitcoin node (node A) sends a hash of the announced block to the victim using Bitcoin INV (Inventory) message. The attacker intercepting the network connection between node A and the victim passes the INV message to the victim. The victim does not hold a newly announced block so it sends the block request via a GETDATA message towards the node A as a response to the INV message.
Note: If the GETDATA request is not answered after 20 minutes by a peer either with a BLOCK or Tx messages, the node disconnects its peer and requests the block from another Bitcoin peer.
The attacker modifies the hash of the requested block in GETDATA messages sent from the victim to node A in order for node A to send an older block to the victim instead of a requested block. The victim receives the older block, ignoring it and waiting for 20 minutes for the delivery of a block that was originally requested. However, the TCP connection is not aborted between node A and the victim since the victim received an answer from node A. Before the 20 minute timeout elapses, once an original block request is sent via GETDATA from a victim to node A, the attacker changes another GETDATA sent from the victim to the Bitcoin node A. The node A sends back the requested information by BLOCK message to the victim. Finally, the victim receives the block that he originally requested. As the message arrives within the 20 minutes time period, node A is not being disconnected by the victim, thus is not being replaced by another peer. However, in the Bitcoin network, where a new block is solved approximately every 10 minutes, the miner wastes almost 20 minutes waiting for the delivery of a requested block.
The delay attack makes merchants susceptible to double spending. Miners waste their computing power and ordinary Bitcoin nodes cannot propagate the latest version of the blockchain. However as Maria Apostolaki in her paper states, due to pools multi-homing, Bitcoin (as a whole) is not vulnerable to delay attacks, even powerful ones. The block can be learnt from another gateway and it can be propagated via this gateway to the Bitcoin network.
Conclusion: Recently, Bitcoin’s price has exceeded the value of $ 5,000 for 1 BTC. Attacks against Bitcoin and other cryptocurrencies become more profitable for attackers, thus they will occur more frequently. The article describes two types of network-based attacks that can possibly disrupt the operation of Bitcoin network. Both attacks use BGP hijacking and can be conducted by attackers who gain access to routers announcing an ASN. The delay attacks are undetectable, but can be prevented by multi-homing when a mining pool becomes connected to different ASs. To detect partition attacks, BGP traffic should be monitored using BGP monitoring services. However, the only reliable mechanism in both cases is to prevent ISPs from installing rogue routes. It can be achieved by various filtering techniques applied by ISPs, but most importantly by securing the BGP protocol, deploying RPKI and BGPsec. In the absence of this being universally adopted, the Bitcoin network should ensure that the prefixes where its nodes reside are being announced as /24.
Automate BGP Routing optimization with Noction IRP

In recent years, the concepts of Artificial Intelligence (AI) and Machine Learning (ML) have moved from the academic...
Recent disruptions to two undersea internet cables in the Baltic Sea have yet again highlighted a pressing issue for...
Understanding BGP states is essential to grasp how BGP operates. Similar to interior gateway protocols (IGPs) like...