Border Gateway Protocol (BGP) is not merely a protocol—it’s the backbone of the...

 Simple Network Management Protocol (SNMP) is a network application layer protocol, initially developed for network management but is now mainly used for network monitoring.
Simple Network Management Protocol (SNMP) is a network application layer protocol, initially developed for network management but is now mainly used for network monitoring.
Each managed network consists of two key components – a network management station (NMS), also called an NMS manager, and one or more SNMP agents (Figure 1).
The agent runs on the managed device and responds to the requests received from the NMS. The agent also sends SNMP traps to NMS to notify of significant alarm events, such as failure of a fan, low power supply voltage, etc.
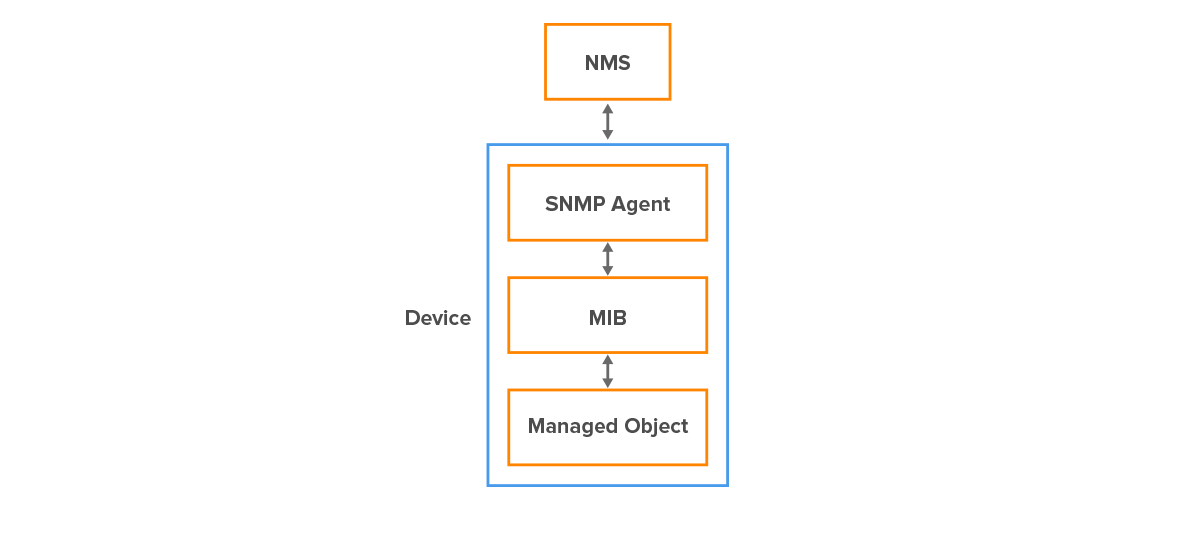
Figure 1 – SNMP Components
The structure of the SNMP Get Response message is depicted in Figure 2. The NMS manager with an IP address 172.31.19.54 has sent SNMP Get request to the agent with an IP 172.31.19.73 to retrieve the value of the variable – OID 1.3.6.1.4.1.253.8.64.4.2.1.7.10.14130104. The Get Response from the agent contains the value of the requested variable – the IP address 172.31.19.2.
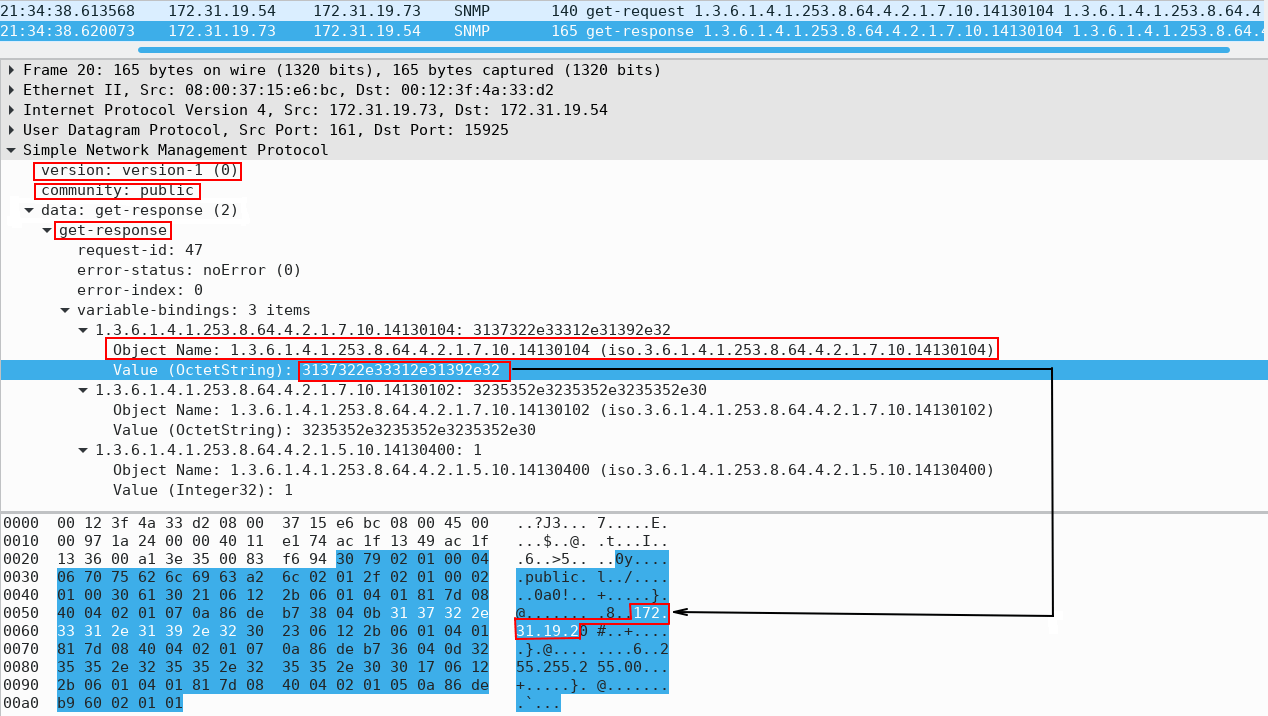
Figure 2 – SNMP Get Request and Response Messages Exchange
A managed device contains several managed objects referred to as object identifiers (OIDs). OID is the identifier that SNMP devices use to manage each entity within the network.
The Management information base (MIB) is a tree-structured file, and the same MIB must be loaded into both the managed devices and the NMS. Device manufacturers typically ship the required MIB files with their SNMP-enabled products.
The MIB serves as an interface between the NMS manager and the agent and allows them to communicate with each other. NMS identifies a managed object based on OID, which is the path starting from the root. For instance, the OID of the interface object depicted in Figure 3 is 1.3.6.1.2.1.2.
If the NMS is configured to monitor an interface variable, it sends a GET request to the agent requesting the value of the OID 1.3.6.1.2.1.2. The NextGet message can be used to retrieve the next object in the list or table within the agent.
1 – International Organization for Standardization (ISO)
3 – Identified organizations according to ISO/IEC 6523-2
6 – US Department of Defense (DOD)
1 – Internet protocol
2 – Internet Engineering Task Force (IETF) management
1 – MIB-2
2 – Interfaces
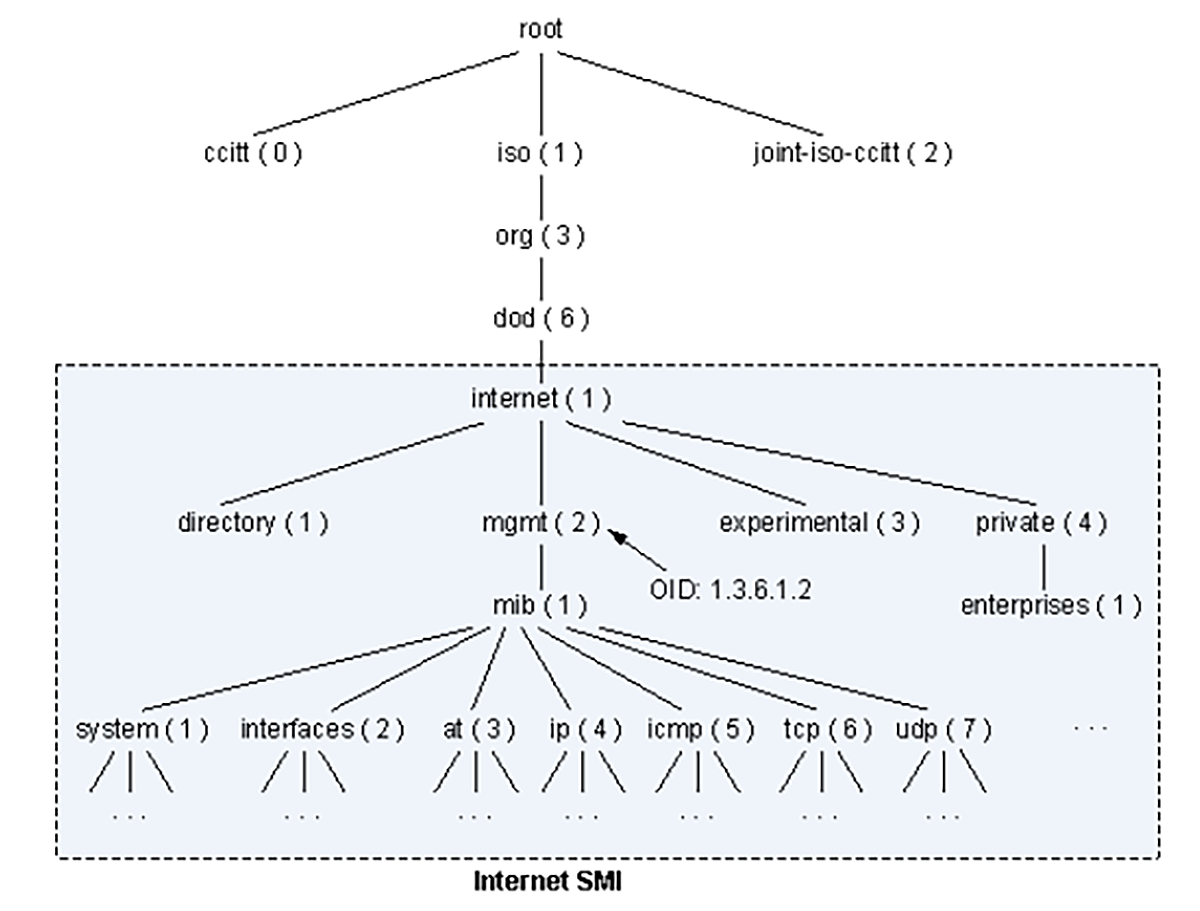
Figure 3 – OID Tree
(https://support.huawei.com/enterprise/en/doc/EDOC1100086963)
SNMP can be also used to set a value of a managed object using SNMP Set operation; for instance to bring the interface down or to set an IP address. Table 1 summarizes the SNMP features along with versions of SNMP for which these features are available.
| Feature | SNMPv1 | SNMPv2c | SNMPv3 |
| Get | Yes | Yes | Yes |
| GetNext | Yes | Yes | Yes |
| Set | Yes | Yes | Yes |
| GetBulk | No | Yes | Yes |
| Trap | Yes | Yes | Yes |
| Inform | No | Yes | Yes |
| Community strings | Yes | No | No |
| User-based security | No | No | Yes |
| Message authentication | No | No | Yes |
| Message encryption | No | No | Yes |
Table 1 – SNMP Features
SNMP has evolved into three versions: SNMPv1, SNMPv2c, and SNMPv3. All SNMP messages are transported via User Datagram Protocol (UDP), and each version supports GET, GetNext, and Set SNMP operations.
The original version of SNMP, referred to as SNMPv1, has critical security and performance limitations.
SNMPv1 provides authentication, which is based on a password (community string). The community string is sent in clear text between the NMS manager and the agents. Therefore, the managed device is vulnerable to unauthorized users who can easily reconfigure the device, especially if IP access control lists (ACLs) are not in place.
The SNMPv1 and 2c data exchanged between the NMS administrator and the agents are not encrypted. For example, the community string in the Get Response depicted in Figure 2 is “public.”
Regarding SNMPv1 protocol performance, the set of protocol transactions is limited to Gets, Sets, and Traps of individual objects in the MIB. Therefore, large sets of information require several transactions to retrieve a row of information.
SNMPv2c is the successor to the original SNMPv1. The standard MIB2 integer is 32 bits long in the case of SNMPv1; SNMPv2 defines a new type of integer that is 64 bits long. A 64-bit counter can better handle high-speed interfaces because 32-bit counters do not provide enough capacity and must wrap quickly. This increases network traffic and has a negative impact on both the agent and the NMS manager CPU utilization.
SNMPv2c also improves the performance of SNMPv1 by introducing the Get Bulk Requests operation. If the NMS manager wants to retrieve a large amount of data, it sends a GetBulk message to the agent instead of a Get request. The GetBulk operation provides values for all variables in the list and is much more efficient than sending repetitive GetNext commands.
SNMpv2c introduces a new type of SNMP communication – SNMP Inform request. Typically, an SNMP Inform is used for manager-to-manager communication to acknowledge receipt of notification. The SNMP inform request packet will be sent continually until the sending SNMP manager receives an SNMP acknowledgment.
Both SNMPv2c and SNMPv1 protocols use simple authentication, which relies on community names.
SNMPv3 is the latest SNMP protocol that addresses the security issues introduced by older SNMP versions. SNMpv3 provides message integrity, authentication, and encryption by implementing SNMP View, SNMP Group, and SNMP User.
SNMP View defines what a particular SNMpv3 user can view. For example, it is possible to configure that a user will only have access to view the interface index, OID 1.3.6.1.2.1.2, and anything below that.
To create an all-access View the name iso should be specified. The MIB has a tree structure so anything below the iso can be accessed (Figure 2).
SNMP Group is associated with the SNMP View and it defines a type of the access – read-only or read/write. It also defines the type of security that is active when interacting with the device.
noauth – nor authentication or encryption auth – only authentication, no encryption priv – authentication and encryption
SNMP User is added to the group with the level of authentication and encryption. The security model must match the group, e.g. priv, a type of the hash for the password (e.g. SHA), the password, encryption algorithm (e.g. AES), and a shared secret for generating encryption keys.
SNMPv1 is obsolete and should not be used anymore. Both SNMPv1 and SNMPv2c provide only simple authentication and do not address encryption. SNMPv2 should only be used in private networks where security is not a major concern. However, the best option is to simply avoid it.
Unlike SNMPv1 and SNMPv2c, SNMP version 3 supports authentication and encryption. This means that SNMP data cannot be read after capture, and only authorized users can access specific object identifiers. However, the additional security methods make SNMPv3 more complex and challenging to configure. The CPU usage, memory utilization, and network traffic overhead caused by authentication and message encryption can increase, especially in networks with many monitored devices and short monitoring intervals. Nevertheless, the additional load is still acceptable, and SNMPv3 is a good choice for monitoring Internet-facing networks.
Both SNMP v2c and v3 support have been introduced to Noction Flow Analyzer starting with v 22.06. Users can now optionally specify credentials for each network device for SNMP polling.
Automate BGP Routing optimization with Noction IRP

In recent years, the concepts of Artificial Intelligence (AI) and Machine Learning (ML) have moved from the academic...
Recent disruptions to two undersea internet cables in the Baltic Sea have yet again highlighted a pressing issue for...
Understanding BGP states is essential to grasp how BGP operates. Similar to interior gateway protocols (IGPs) like...