Border Gateway Protocol (BGP) is not merely a protocol—it’s the backbone of the...

 When it comes to major security concerns, one of the most serious ones are the data breaches and security exploits caused by insider incidents. According to the “2018 Cost of Insider Threats: Global Study” benchmark study produced by Ponemon Institute LLC, 159 interviewed organizations experienced a total of 3,269 insider incidents over the past 12 months. The research was completed in January 2018 based on interviews with 717 IT and IT security practitioners in 159 organizations from North America (the US and Canada), Europe, Middle East & Africa, and Asia-Pacific. Targeted entities were business organizations with a global headcount of 1,000 or more employees [1].
When it comes to major security concerns, one of the most serious ones are the data breaches and security exploits caused by insider incidents. According to the “2018 Cost of Insider Threats: Global Study” benchmark study produced by Ponemon Institute LLC, 159 interviewed organizations experienced a total of 3,269 insider incidents over the past 12 months. The research was completed in January 2018 based on interviews with 717 IT and IT security practitioners in 159 organizations from North America (the US and Canada), Europe, Middle East & Africa, and Asia-Pacific. Targeted entities were business organizations with a global headcount of 1,000 or more employees [1].
Most incidents in this research were caused by insider negligence. Specifically, the careless employee or contractor was the root cause of almost 2,081 of the 3,269 reported incidents. To deal with the consequences of insider incidents, large organizations, with a headcount of more than 75,000, spent an average of $2,081 million over the past year. Smaller-sized organizations, with a headcount below 500, spent an average of $1.80 million to deal with insider-related incidents. Companies in financial services, energy & utilities, and industrial & manufacturing incurred an average cost of $12.05 million, $10.23 million and $8.86 million, respectively.
The research reveals that all types of insider risk threats have increased since the initial study conducted in 2016. The average number of incidents involving employee or contractor negligence has increased from 10.5 to 13.4. The average number of credential theft incidents has tripled over the past two years, from 1.0 to 2.9.
In the context of the findings brought by Ponemon’s study, it seems that the ability to prevent, detect and respond to internal security incidents becomes crucial. However, this can be hardly achieved without deeper understanding of employees’ behavior and actions. Vanishing perimeter caused by cloud adoption, the plethora of BYOD devices, remote workers on one side and an increasing number of internal incidents on the other, emphasizes the importance of monitoring and analysis of the east-west user traffic. Malware, worms, and botnets cause changes in network traffic that can be easily detected by analyzing Flexible NetFlow data. The data is also a valuable forensic tool that can help to understand and replay the history of security incidents.
Picture 1 depicts a Flexible NetFlow record that captures network statistics from communication between the internal Linux management workstation 192.168.0.1 and the host on the Internet – 195.165.0.1. What seems to be a legitimate HTTP communication is, in fact, a reverse shell created for the purpose of bypassing a border firewall, to access the internal network from outside. Obviously, the connection must be initiated from the client, which is the workstation 192.168.0.1 to the attacker’s server 195.165.0.1. Of course, further investigation including log analysis is needed to determine if it is a work of a disgruntled employee or else. However, it is clear that a security solution using NetFlow records as data input should bring an alarm because http parameters such as user-agent or uri are missing.
| Note: Insider threat is a generic term for a threat to an organization’s security or data that comes from within. Such threats are usually attributed to employees or former employees, but may also arise from third parties, including contractors, temporary workers or customers. [2]. Internal network traffic is commonly referred to as east-west network traffic. Traffic that crosses a perimeter is referred to as north-south traffic. |
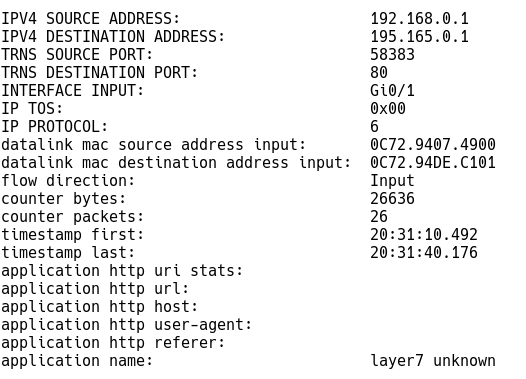
Picture 1: Reverse Shell Flexible NetFlow Record
So, what are the benefits of NetFlow for the detection of malicious traffic caused by insider threats? Firstly, existing network devices can be used as distributed sensor nodes so there is no additional cost associated with the implementation of such devices. Secondly, multiple NetFlow sensors provide a wide picture of concurrent network activity. The third benefit lies in the aggregated nature of Flexible NetFlow. Flows are created based on particular criteria, specified by match statement and exported from sensors to a centralized point. However, only network metadata gets exported to a flow collector. Therefore, data can be processed efficiently in real-time or near to real-time on the collector. This approach allows us to scale high-speed rates (Gigabits per second) and reduce the amount of exported data. The universal formula is that NetFlow traffic represents about 1.5% to 3% of the total traffic seen by an exporter. For instance, if a single Ethernet frame (1500 Bytes) carries about 24-30 flows and a flow exporter is exporting 3000 flows-per-seconds to the collector, it is about 1.5 Mbps (1500 / 24 * 3000 * 8). Last but not least, the privacy of users is granted as only network metadata are collected. Therefore, no sensitive information such as the user’s credentials is exported.
A Network Traffic Analysis solution based exclusively on NetFlow record analysis can detect DoS/DDoS attacks, web application and SSH compromise, Botnet activity, and other malicious traffic. While it provides Layer 7 application visibility by gathering application information, a tool should use this method in combination with other techniques. These include supervised and unsupervised machine learning, deep learning, deep packet inspection, and advanced analytics to detect malicious network behaviors and suspicious traffic. These techniques allow the use of behavioral analysis in addition to signature-based analysis to detect network anomalies caused by unknown or future threats.
In recent years, the concepts of Artificial Intelligence (AI) and Machine Learning (ML) have moved from the academic...
Recent disruptions to two undersea internet cables in the Baltic Sea have yet again highlighted a pressing issue for...
Understanding BGP states is essential to grasp how BGP operates. Similar to interior gateway protocols (IGPs) like...