Border Gateway Protocol (BGP) is not merely a protocol—it’s the backbone of the...

 This is the second part of the post dedicated to NetFlow configuration. In the first part, we’ve discussed the configuration of Flexible NetFlow on Cisco IOS device and the configuration of j-Flow v8 on Juniper vSRX security appliance.
This is the second part of the post dedicated to NetFlow configuration. In the first part, we’ve discussed the configuration of Flexible NetFlow on Cisco IOS device and the configuration of j-Flow v8 on Juniper vSRX security appliance.
In this part we will go further and explain NetFlow v9 configuration on an open-source VyOS router and the configuration of NetStream Flexible Flow exporting on the Huawei AR G3 AR3200 Series router.
VyOS is an open-source router based on Debian and FRRouting with the configuration syntax similar to JUNOS from Juniper Networks. The VyOS appliance connected in our network topology (Picture 1) will be configured for collecting and exporting the flow statistics NetFlow v9.
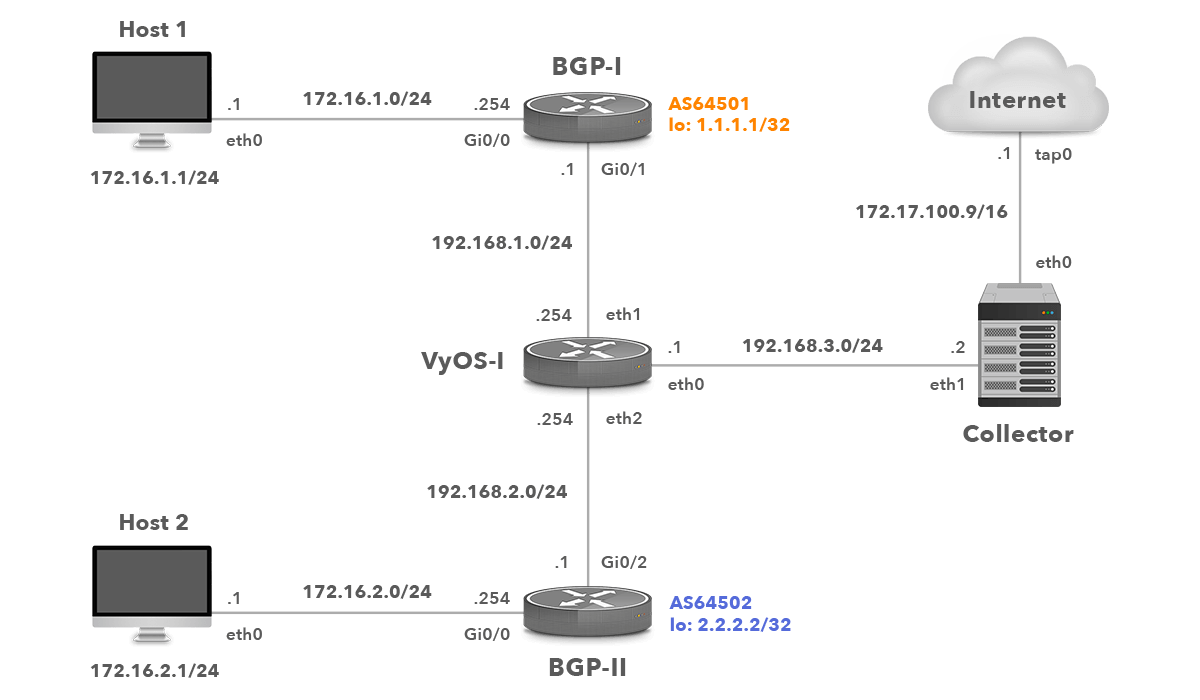
Network Topology with VyOS
vyos@vyos:~$ configure vyos@vyos# set system flow-accounting interface eth1
Enter the command for each interface you want to monitor.
vyos@vyos# set system flow-accounting netflow server 192.168.3.2 port 2055
NetFlow data will be exported to the NetFlow collector with the IP address 192.168.3.2 listening on port 2055.
Configure the rate at which packets are sampled for statistics. The smaller the sample rate, the bigger the impact on CPU and the amount of exported data. A sample rate of 1 provides 1:1 packet sampling, which will log every packet. Therefore, avoid a sampling input rate of 1.
vyos@vyos# set system flow-accounting netflow sampling-rate 100
One packet will be accounted for every 100 packets.
Specify NetFlow Format that data will be exported in.
vyos@vyos# set system flow-accounting netflow version 9
Specify a flow expiration timeout in seconds at which Netflow data will be sent to a Netflow collector.
vyos@vyos# set system flow-accounting netflow timeout expiry-interval 60
The active flow timeout is set to 1 minutes. This is the default value.
Specify a maximum active life timeout in seconds.
vyos@vyos# set system flow-accounting netflow timeout max-active-life 604800
To display NetFlow cache, issue the command from VyOS CLI.
vyos@vyos:~$ show flow-accounting interface eth1
They are three flows recorded in the cache with the total packet count 136 (137 Bytes) (Picture 2). The first three lines represent SSH connection from PC1 (172.16.1.1) to PC2 (172.16.2.1). The last line records BGP traffic sent from the router BGP-1 (1.1.1.1), source TCP port 179 to the router BGP-2 (2.2.2.2).
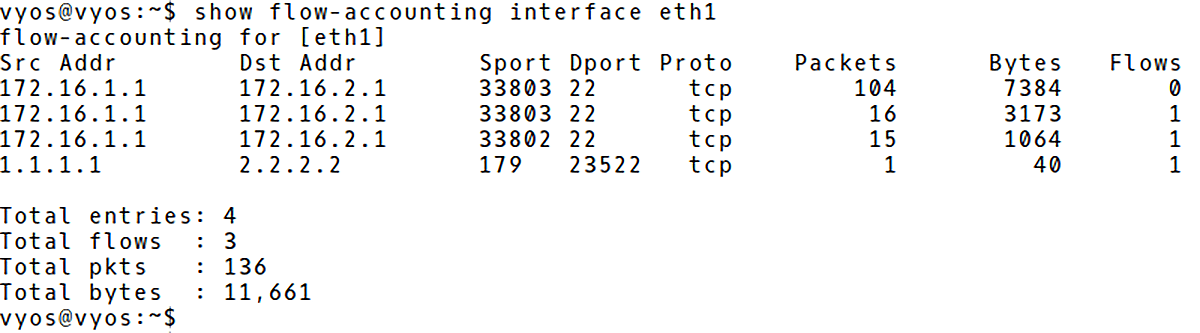
Picture 2: VyOS NetFlow Cache
The flow statistics can be easily deleted with the command:
vyos@vyos:~$ clear flow-accounting counters
We will simulate a DDoS attack with hping utility and check the flow records again. The attacker (172.16.1.1) is flooding the victim (172.16.2.1) from a number of spoofed source addresses, the destination TCP port 22. The aim of the attack is to prevent legitimate users to use SSH service.
$ sudo hping3 -c 10000 -d 1200 -S -w 64 -p 22 --flood --rand-source 172.16.2.1 -c count -> number of sent packets -d -> data size 120 bytes -S -> set SYN flag -w -> win size -p destination (victim) port - SSH --flood -> sent packets as fast as possible. Don't show replies --rand-source -> random source address mode 172.16.2.1 -> destination (victim address)
They are many flows counting 1 packet (1240Bytes) recorded in the VyOS flow cache (Picture 3).
vyos@vyos:~$ show flow-accounting interface eth1
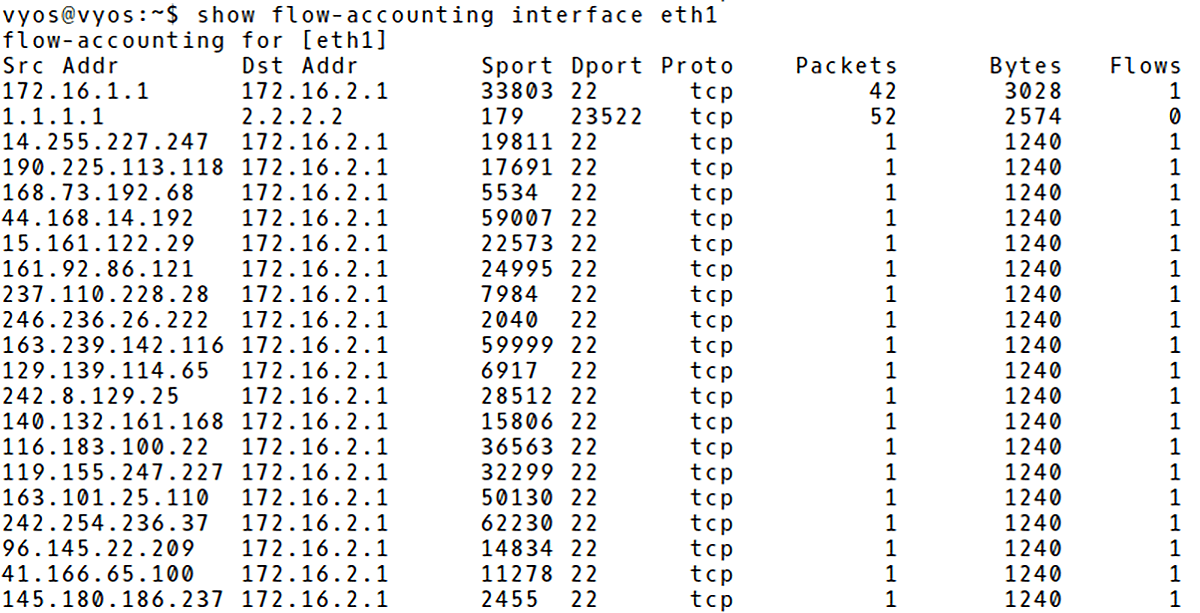
Picture 3: Recorded DDoS Attack in VyOS Flow Cache
We can filter the output of the cache based on the host, port or top parameter. For instance, to display only flow statistic about BGP traffic, issue the command below (Picture 4).
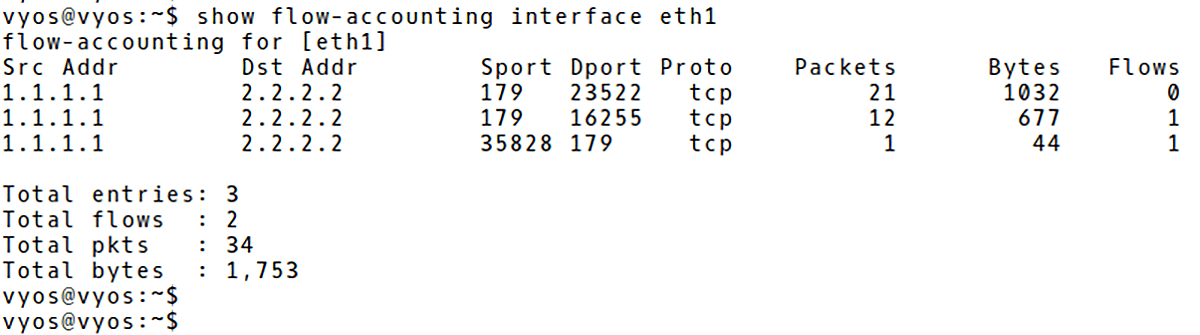
Picture 4: Filtering VyOS Flow Cache for BGP Traffic
To display top N talkers, filter the output using the top parameter (Picture 5). The command displays only top 10 talkers.
vyos@vyos:~$ show flow-accounting interface eth1 top 10
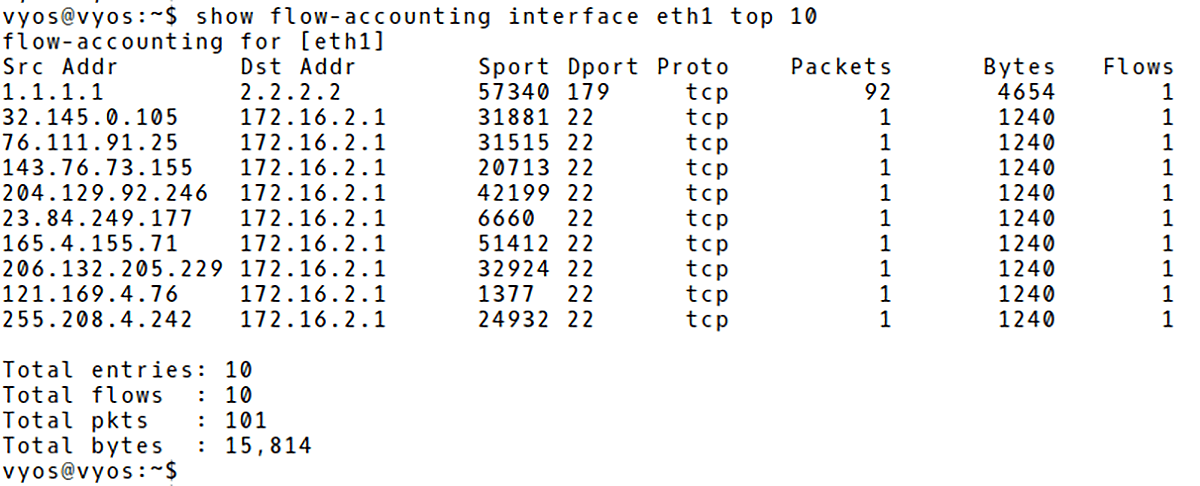
Picture 5: Top 10 Talkers in VyOS NetFlow Cache
NetStream is a traffic statistics and analysis technology from Huawei Technologies. It can collect, store and export statistics about flows in order to monitor and analyze network traffic. NetStream flow statistics exporting modes are: original flow exporting, aggregation flow exporting and flexible flow statistics exporting. Compared to original flow statistics exporting, flexible flow statistics exporting occupies less traffic and provides users with a flexible way to collect NetStream statistics [1].
Flexible flows are established based on customized flow record configuration. Users can configure flow statistics collection based on the protocol type, DSCP field, source IP address, destination IP address, source port number, destination port number, or flow label, as required.
We will show the configuration of Flexible flows exporting on the Huawei Integrated Enterprise Router AR3260 in a role of the NetStream Data Exporter (NDE). The network topology is depicted in Picture 6.
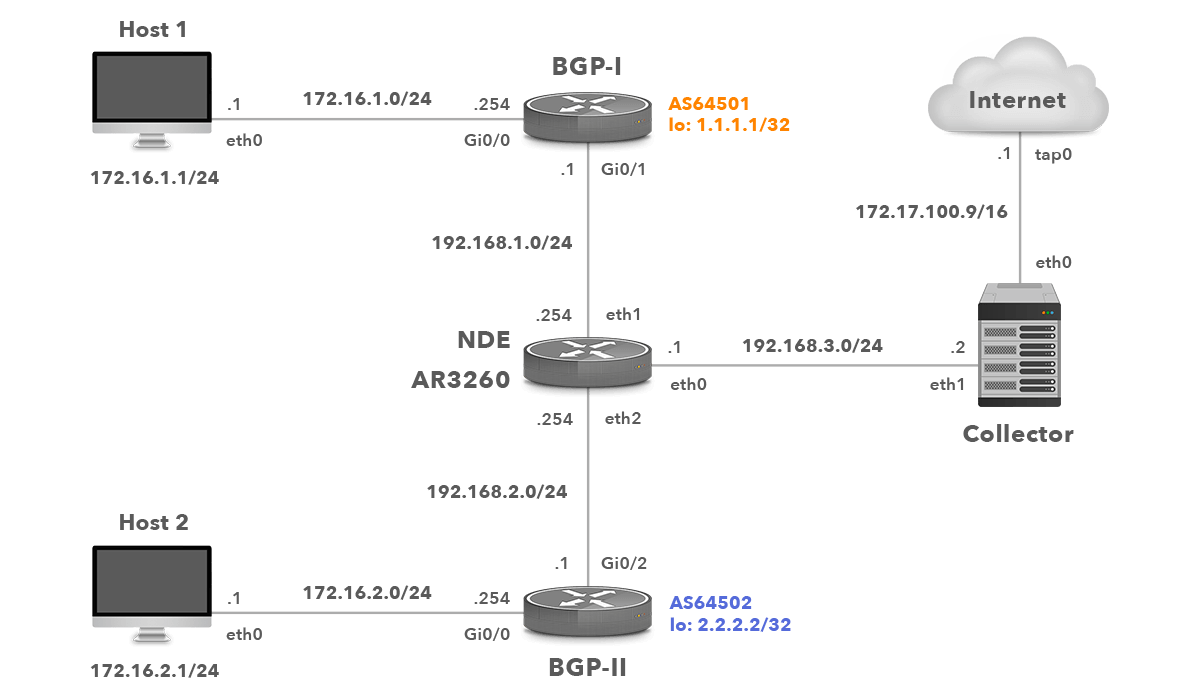
Picture 6: Network Topology with Huawei NDE
Create a flexible flow statistics template test. Let’s collect the number of bytes and packets in the exported packets based on the destination address/port and configure the indexes of the inbound and outbound interfaces.
system-view [AR3260] ip netstream record myrecord [AR3260-record-myrecord] match ipv4 destination-address [AR3260-record-myrecord] match ipv4 destination-port [AR3260-record-myrecord] collect interface input [AR3260-record-myrecord] collect interface output [AR3260-record-myrecord] collect counter bytes [AR3260-record-myrecord] collect counter packets [AR3260-record-myrecord] quit
Set the source IP address of the exported packets carrying flexible flow statistics to the IP address of the NDE 192.168.3.1. The destination IP address of the NetStream stream collector (NSC) is 192.168.3.2 with the destination UDP port number 2050.
[AR3260] ip netstream export source 192.168.3.1 [AR3260] ip netstream export host 192.168.3.2 2050
We use a flexible netflow statistics export, therefore a version of the exported NetFlow packets is set to v9.
[AR3260] ip netstream export version 9
Active aging enables the NDE to periodically export the statistics about the flows that last for a long time period. After the active aging timer expires, the flow statistics are exported. We will set the active aging time of IPv4 flows in minutes. By default, the active aging time of IPv4 flows is 30 minutes.
[AR3260] ip netstream timeout active 30
Inactive aging enables NDE to export the statistics about flows that last for a short period. Once adding packets to a flow stops, NDE exports the flow statistics to NSC in order to save the memory space. Set the inactive time of IPv4 flows in seconds. By default, the inactive aging time of IPv4 flows is 30 seconds.
[AR3260] ip netstream timeout inactive 30
Enable flexible flow statistics exporting on the interface ge/0/0/1, and apply the flexible flow statistics template myrecord to the interface
[AR3260] interface gigabitethernet 0/0/1 [AR3260-GigabitEthernet0/0/1] port ip netstream record myrecord [AR3260-GigabitEthernet0/0/1] ip netstream inbound [AR3260-GigabitEthernet0/0/1] ip netstream outbound [AR3260-GigabitEthernet0/0/1] quit
Now, let’s introduce three commands that can be helpful in the process of NDE operation troubleshooting.
The configuration settings can be checked with the command below (Picture 7). You can find here information such as the IP address of NDE (192.168.3.2), The IP of the NSC (192.168.3.1), active and inactive timers, NetFlow exported version (v9), the template and the interface NetStream is enabled on.
<AR3260> display ip netstream
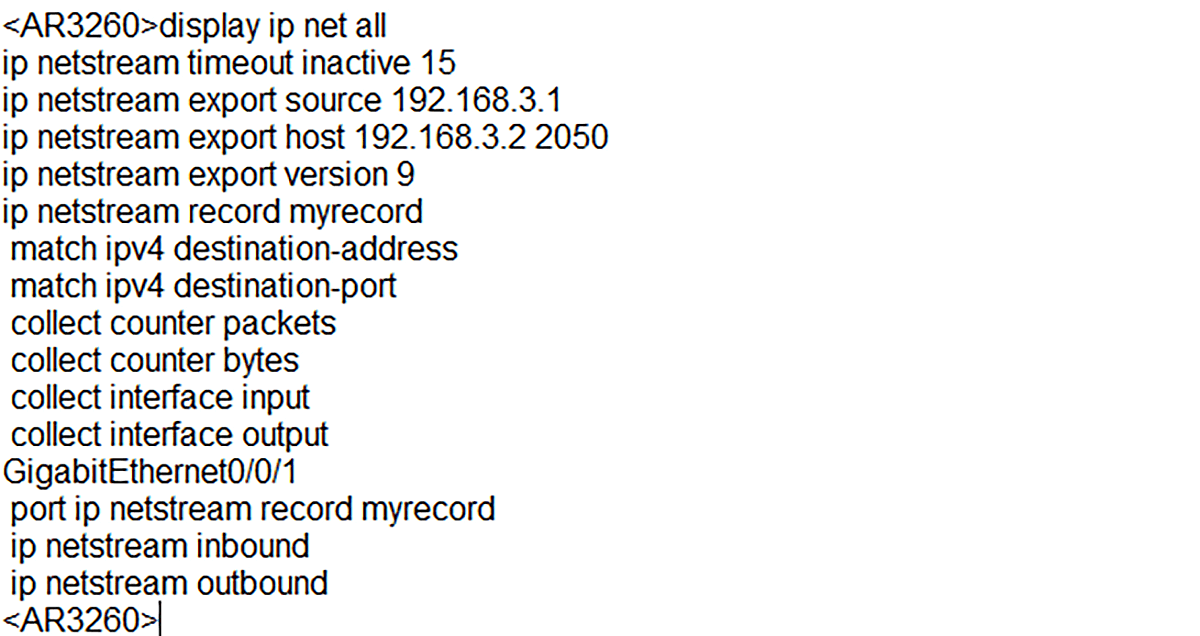
Picture 7: Displaying Configuration Settings
Statistic can be checked with the command below (Picture 8).
<AR3260> display ip netstream statistic
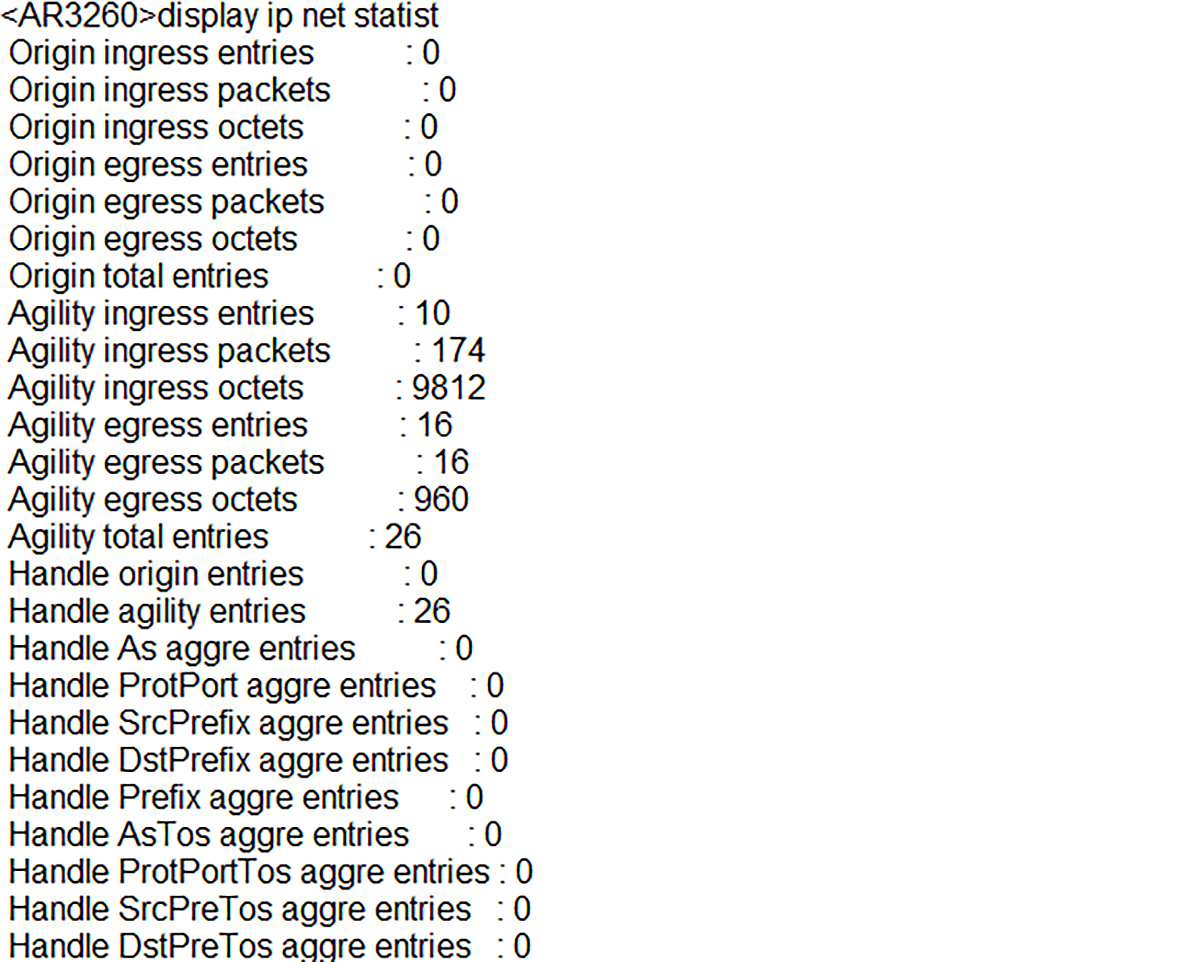
Picture 8: Checking NetStream Statistics
And finally, let’s display the content of the NetFlow cache with the command below (Picture 9).
<AR3260> display ip netstream cache
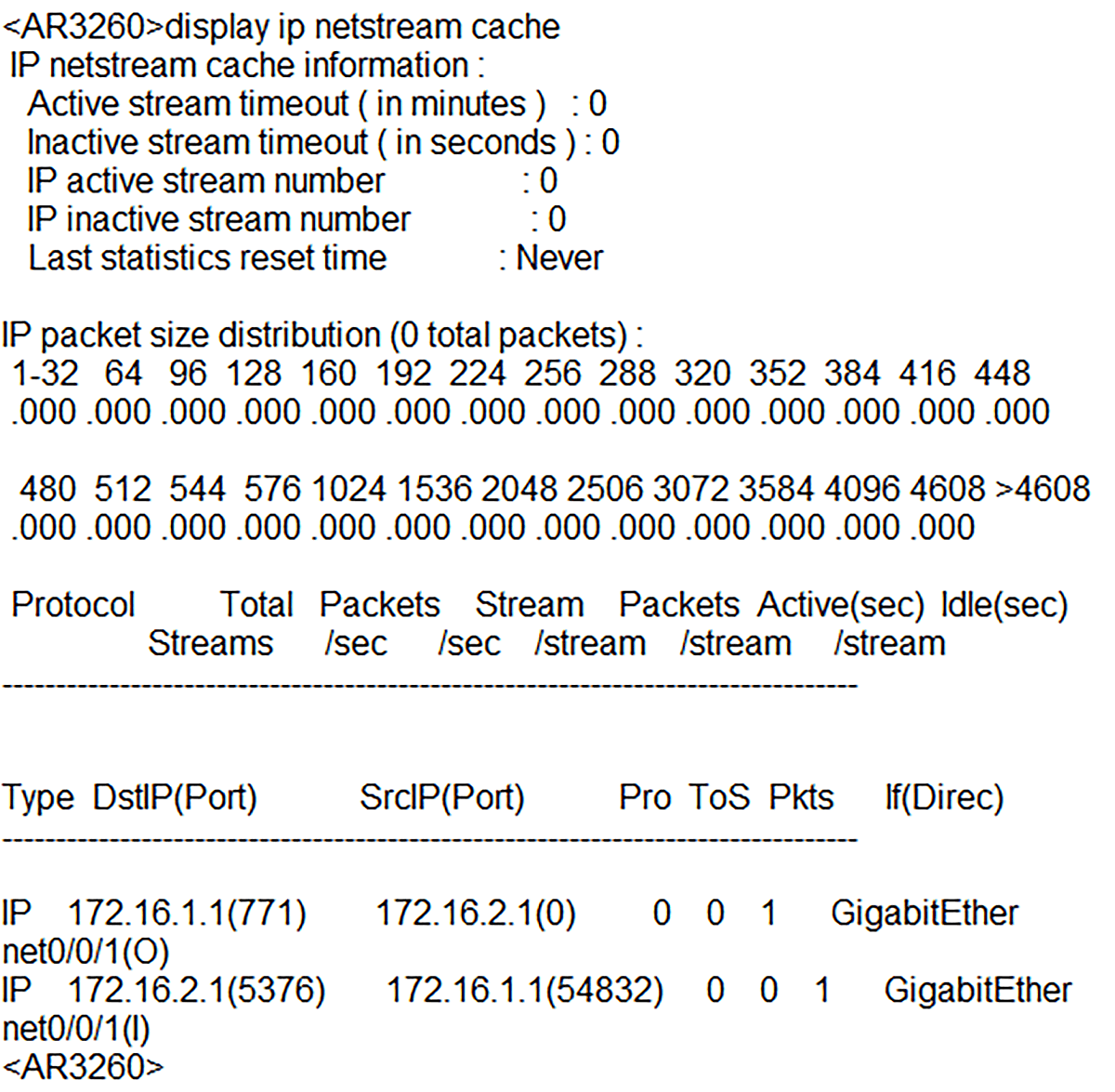
Picture 9: Checking Content of NetStream Cache
Although the syntax of NetFlow configuration differs across vendors, as they use different CLI, there is the same logic behind the configuration when the RFC is followed. All we need to do is to define an interface used for collecting statistics, a direction, the IP addresses of exporters and collector, NetFlow version, the active and inactive timers and possibly a sampling rate. If Flexible NetFlow is a requirement, matching parameters such as IPv4 source and destination address, source and destination ports and counters must be configured for a flow record template. Equipped with this information, every network engineer can easily configure NetFlow if needed.
Read this article in French – La configuration de NetFlow sur les périphériques réseau VyOS et Huawei
In recent years, the concepts of Artificial Intelligence (AI) and Machine Learning (ML) have moved from the academic...
Recent disruptions to two undersea internet cables in the Baltic Sea have yet again highlighted a pressing issue for...
Understanding BGP states is essential to grasp how BGP operates. Similar to interior gateway protocols (IGPs) like...